https://h.dayi.ink/posts/2/#more
title: 网络系统集成基础(实验学时)——实验八
date: 2024-07-02 11:27:12
tags:
网络系统集成基础(实验学时)——实验八
实验八 校园网设计、广域网链接及认证
实验内容:
1、广域网链接PPP协议及认证(PAP认证、CHAP认证)。
2、防火墙区域配置
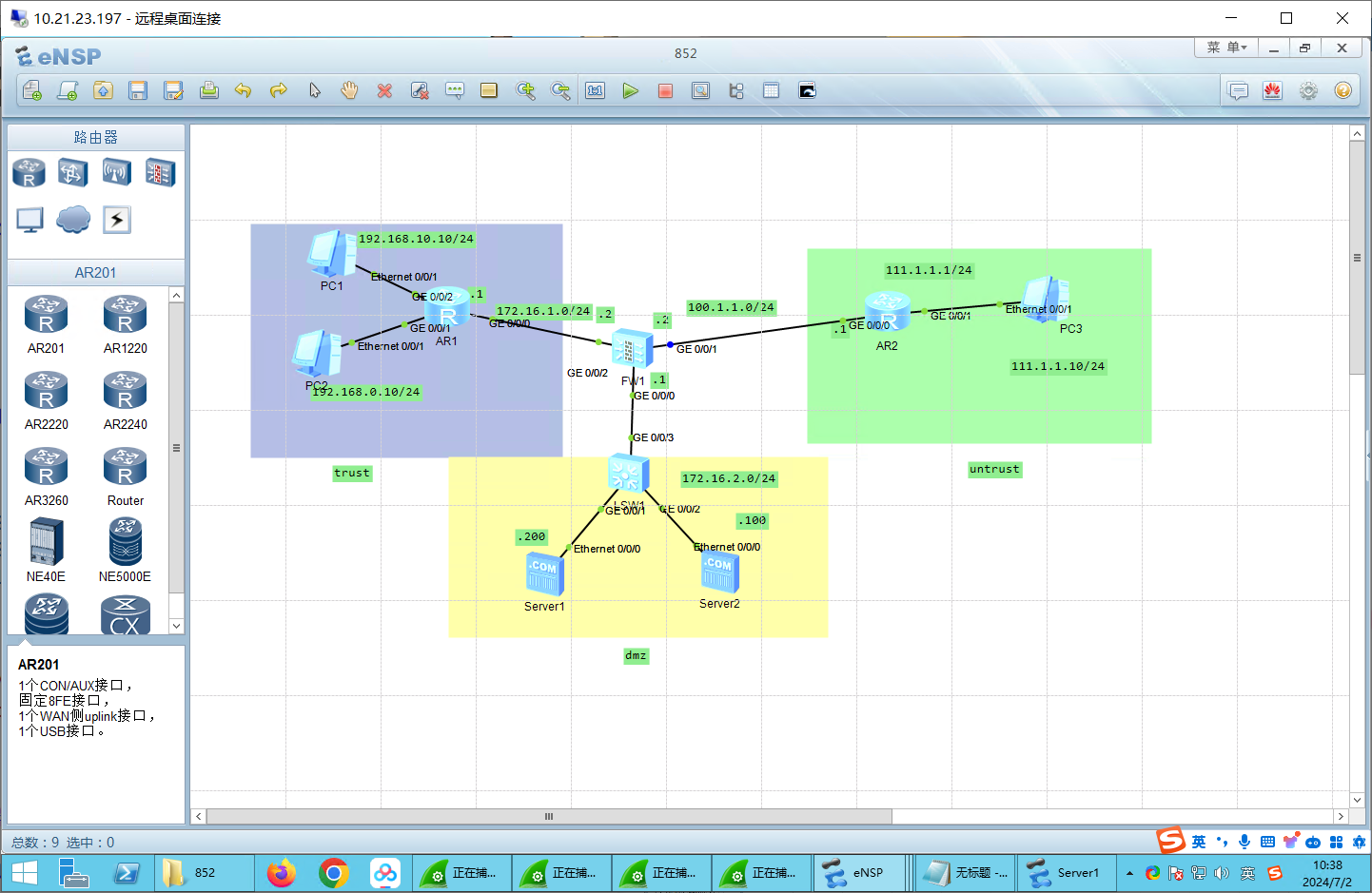
3、参考给定资料,设计山东科技大学校园网络(黄岛校区+泰安校区)。
实验报告:
要求独立完成,报告需包含模拟器配置文件
使用华为模拟器或思科模拟器完成
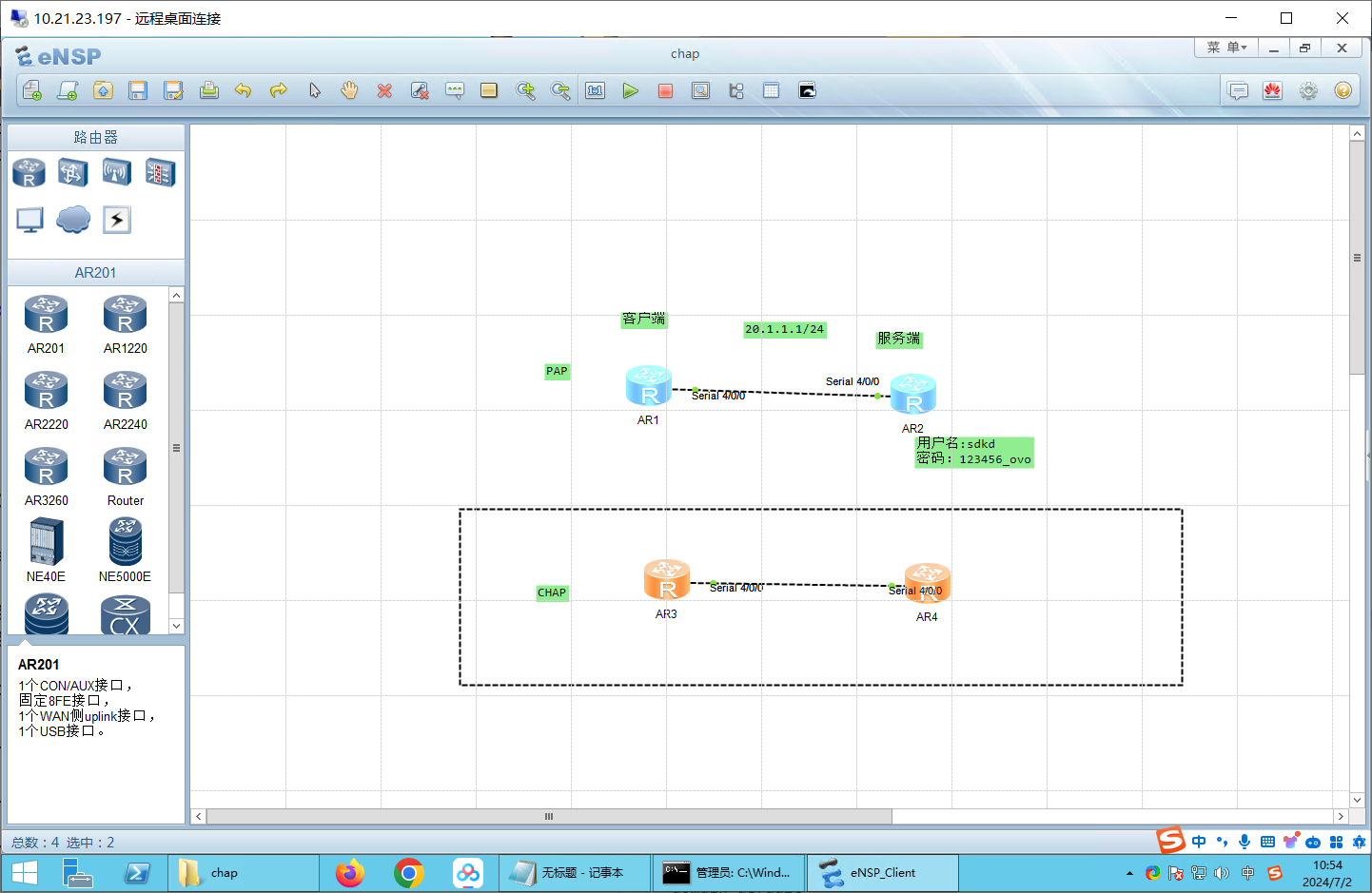
1、广域网链接PPP协议及认证(PAP认证、CHAP认证)。
添加模块:2SA
用串口线连接上:
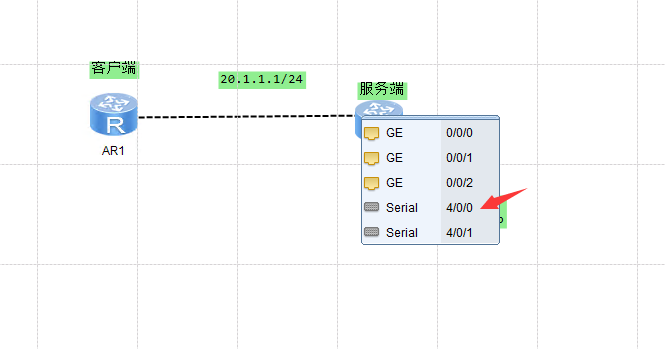
先配置IP地址
R1:
<Huawei>sys
Enter system view, return user view with Ctrl+Z.
[Huawei]int s4/0/0
[Huawei-Serial4/0/0]ip addr 20.1.1.1 24R2:
<Huawei>sys
Enter system view, return user view with Ctrl+Z.
[Huawei]int s4/0/0
[Huawei-Serial4/0/0]ip addr 20.1.1.2 24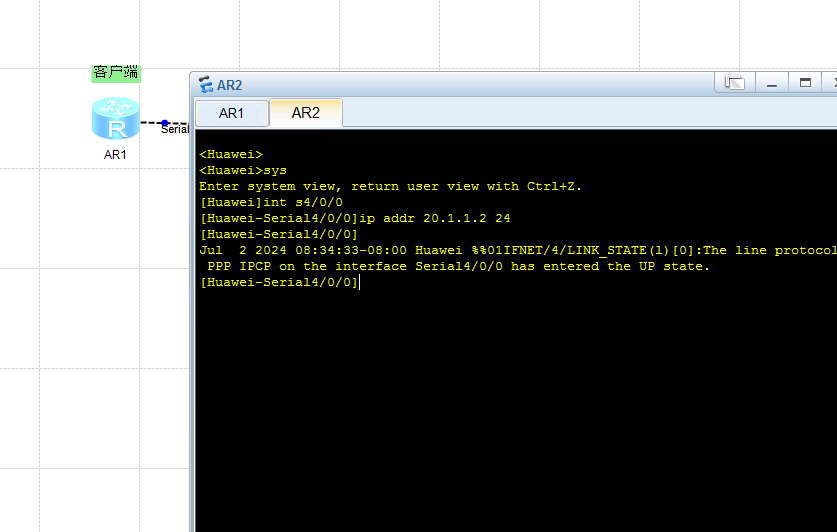
先开始抓包
在S4/0/0上开始抓包即可。
配置PAP:本地验证
服务端(R2):
aaa
local-user sdkd password cipher kd123456_ovo
local-user sdkd service-type ppp
int s4/0/0
ppp authentication-mode pap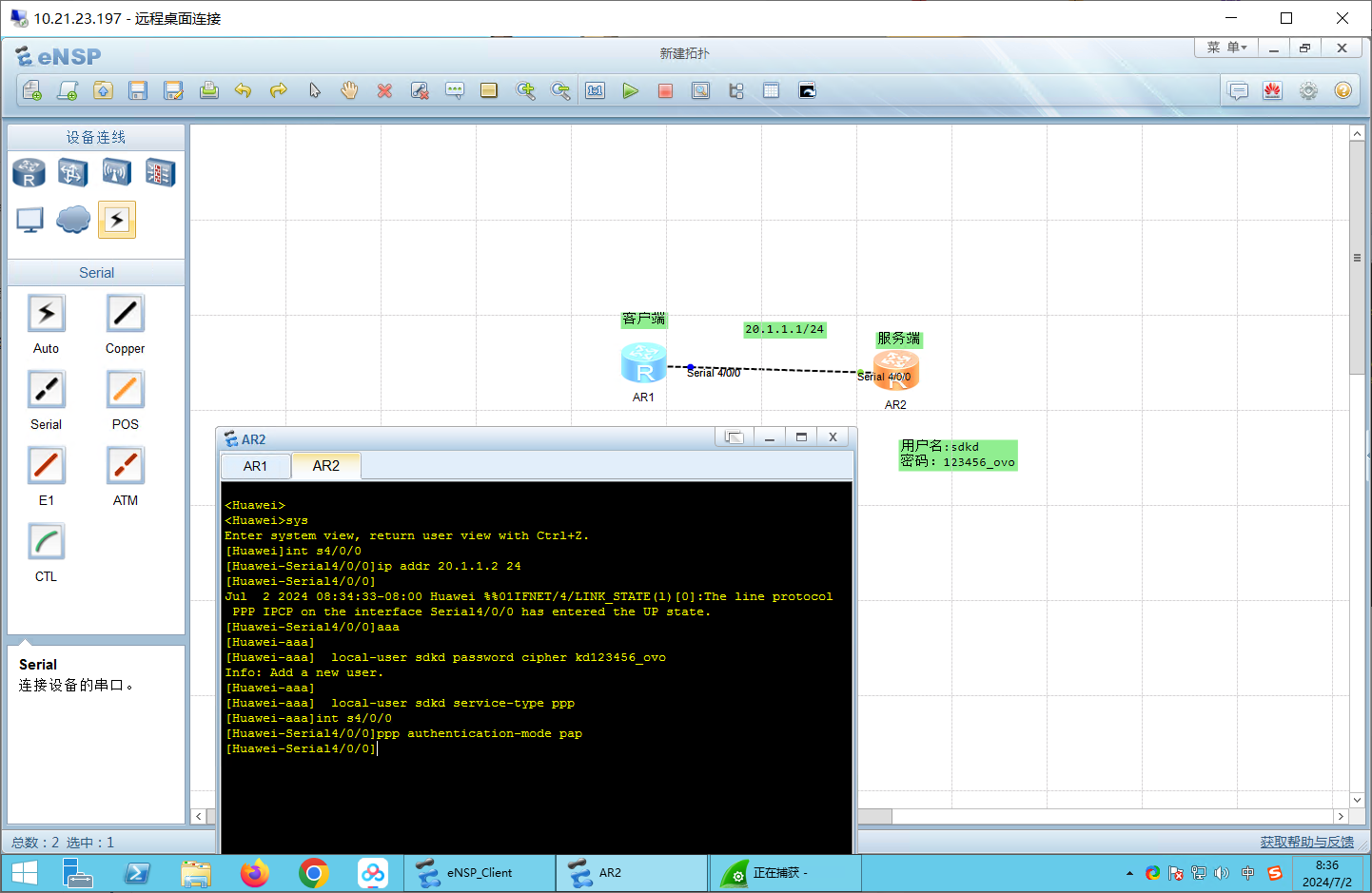
客户端(R1):
int s4/0/0
ppp pap local-user sdkd password simple kd123456_ovo
int s4/0/0
shutdown
undo shutdown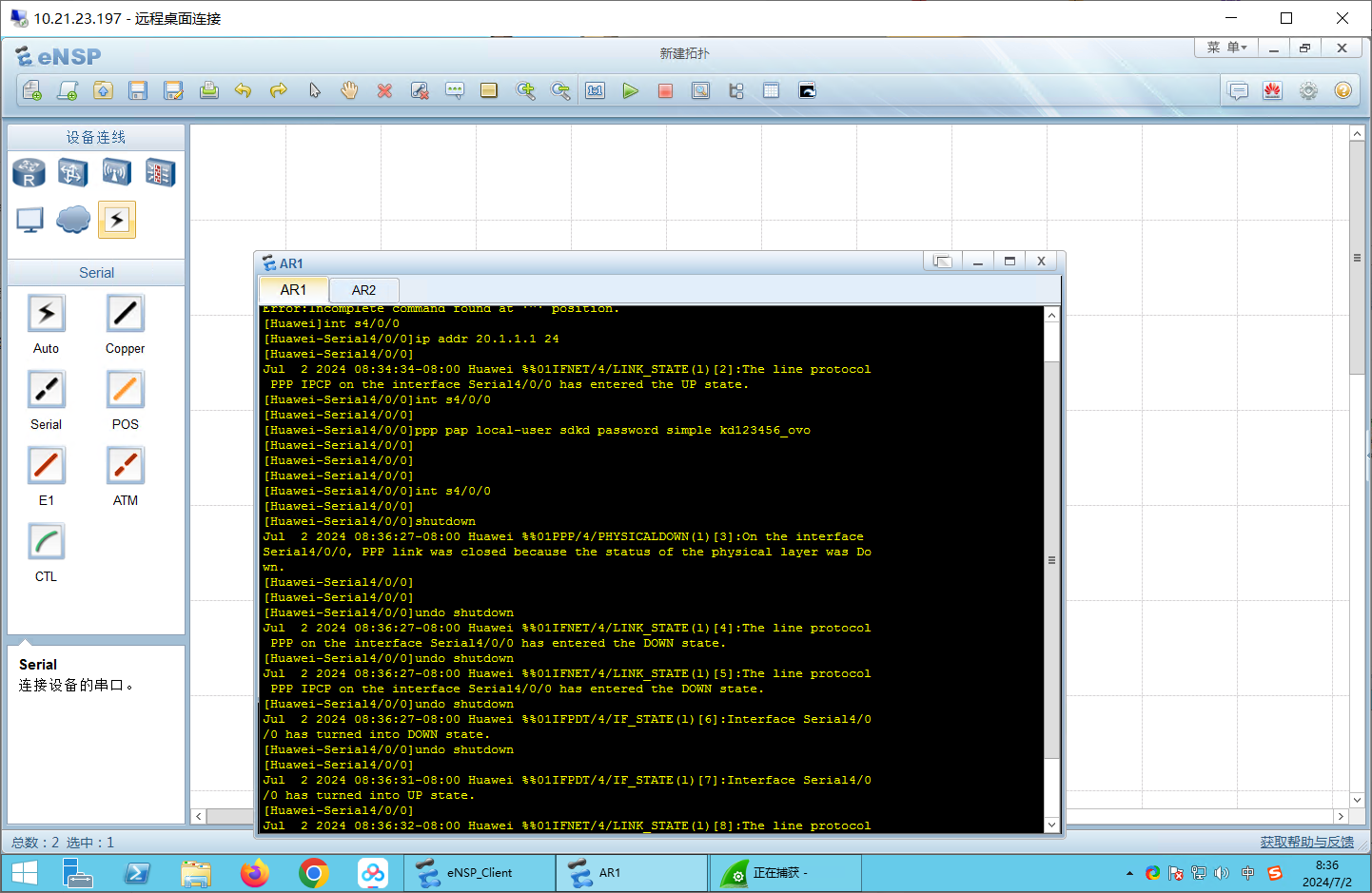
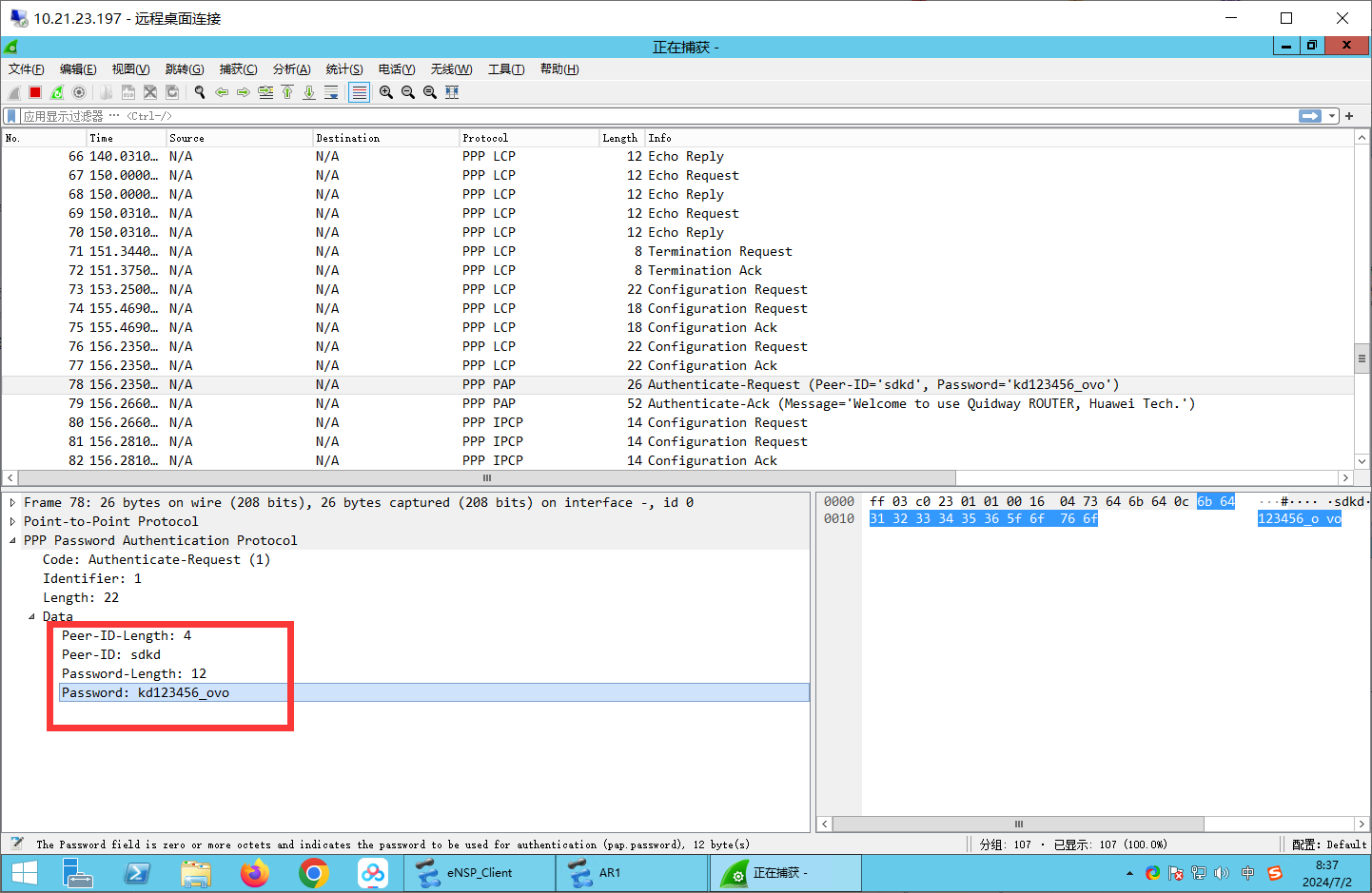
抓包:
验证密码:
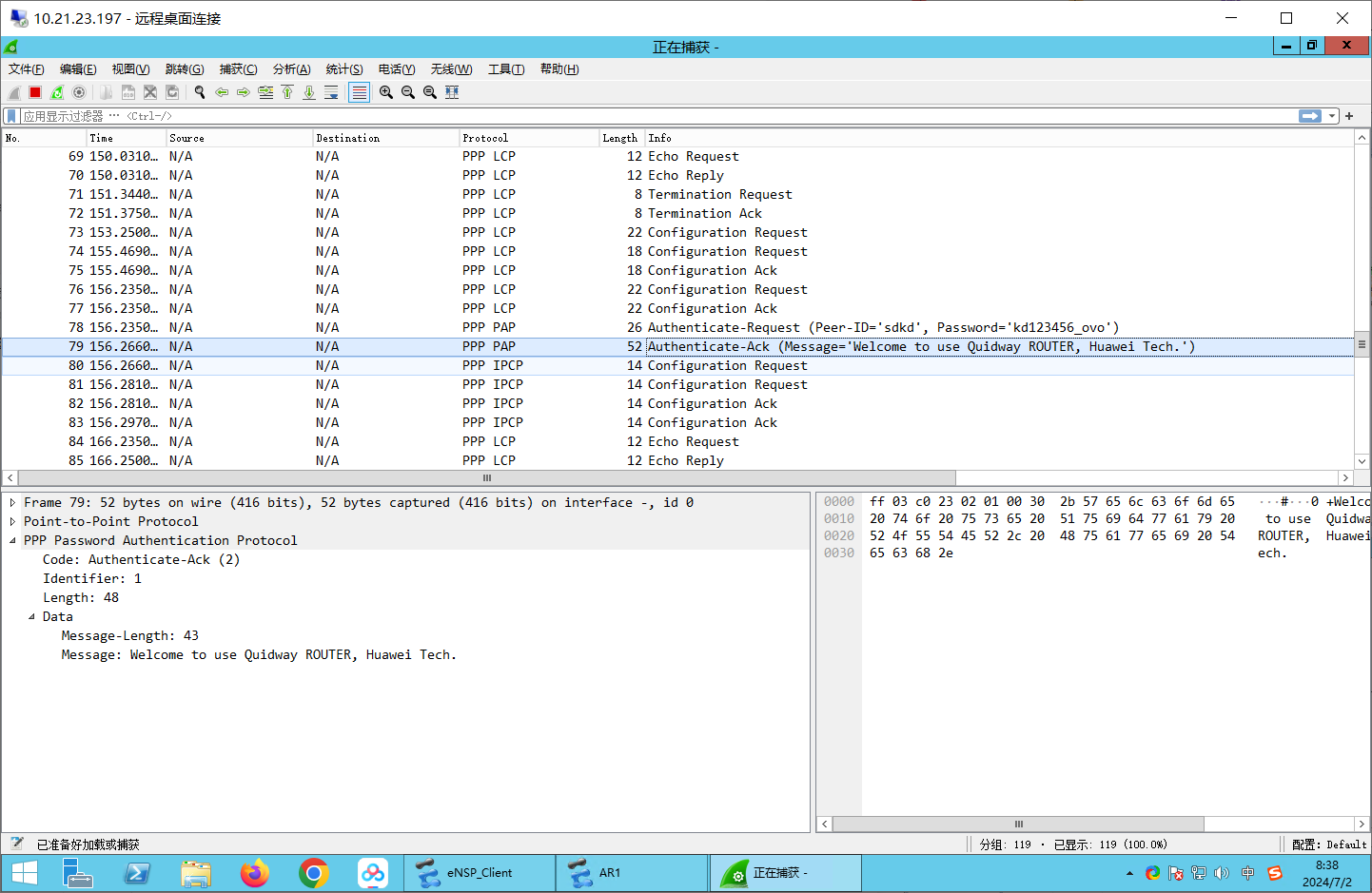
可见已经建立成功了:
配置CHAP
记得先开始抓包
抓包在s4/0/0上。
配置IP地址
同上文
[Huawei]undo info-center enable
Info: Information center is disabled.
[Huawei]int s4/0/0
[Huawei-Serial4/0/0]ip addr 20.1.1.1 24
[Huawei]int s4/0/0
[Huawei-Serial4/0/0]ip addr 20.1.1.1 24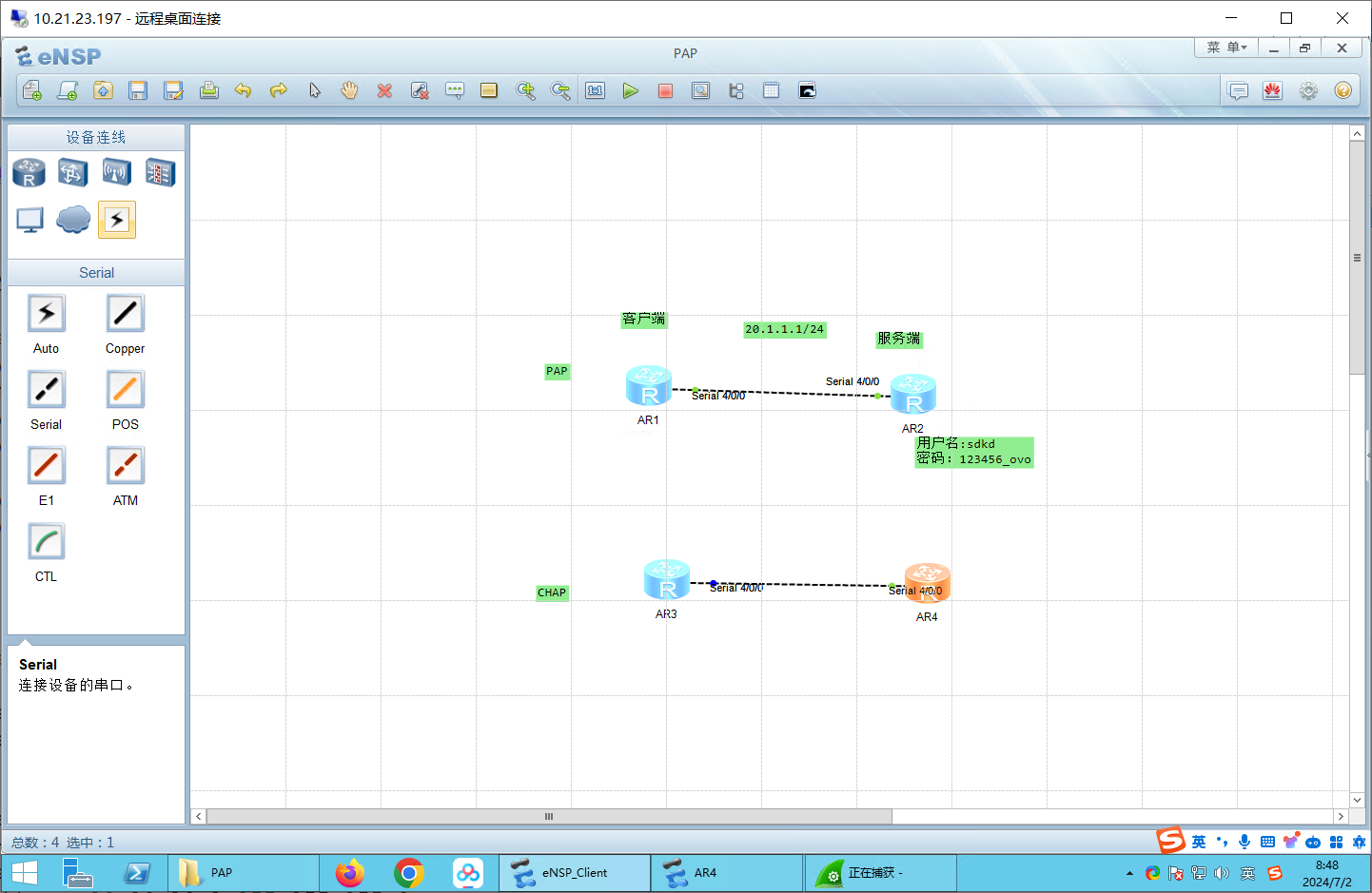
CHAP:配置验证
服务端:R4
undo info-c enable
aaa
local-user sdkd password cipher 123456_ovo
local-user sdkd service-type ppp
int s4/0/0
link-protocol ppp
ppp authentication-mode chap
ip address 20.1.1.2 255.255.255.0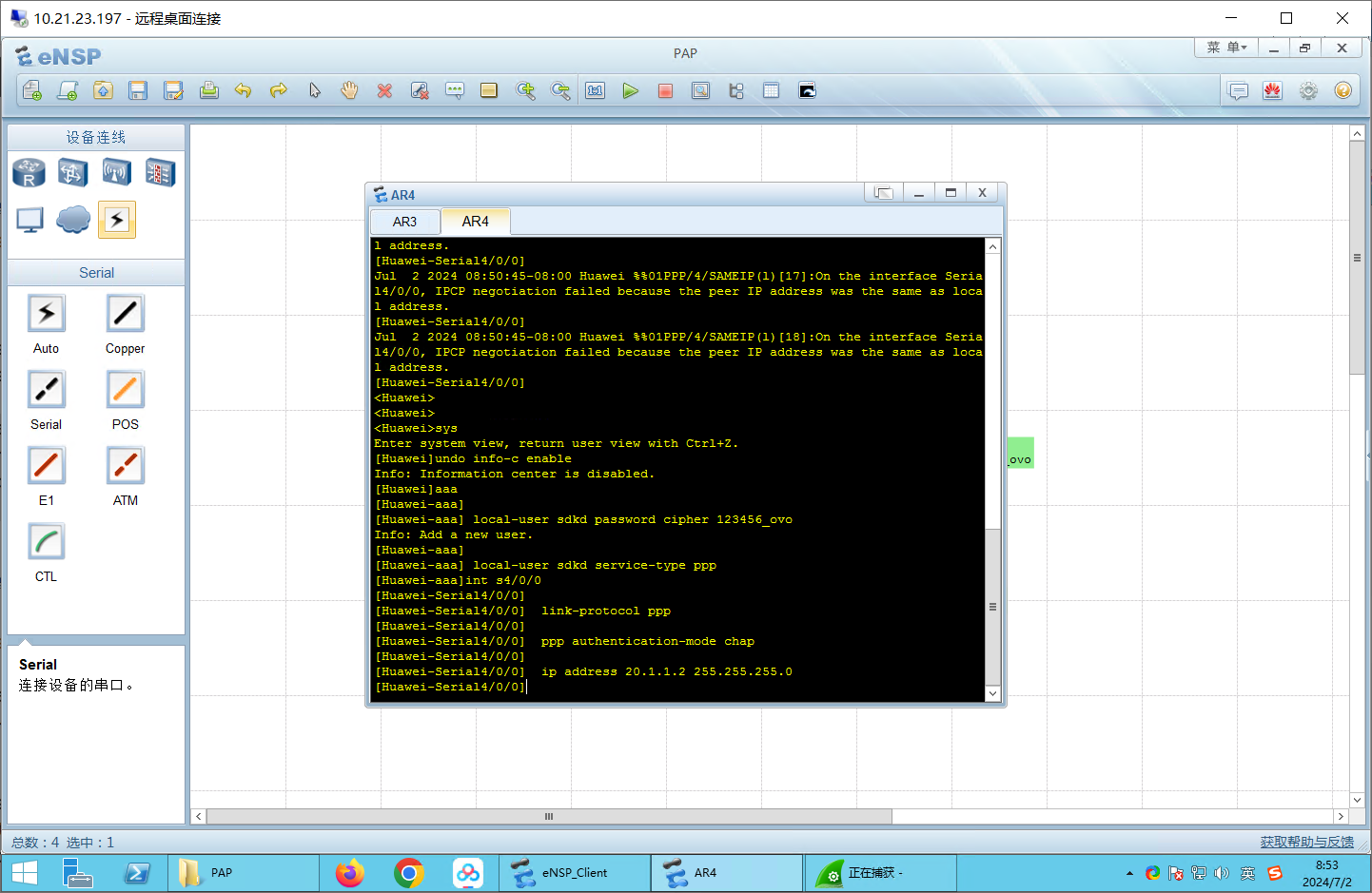
客户端:R3
undo info-c enable
int s4/0/0
link-protocol ppp
ppp chap user sdkd
ppp chap password cipher 123456_ovo
ip address 20.1.1.1 255.255.255.0
shut
undo shut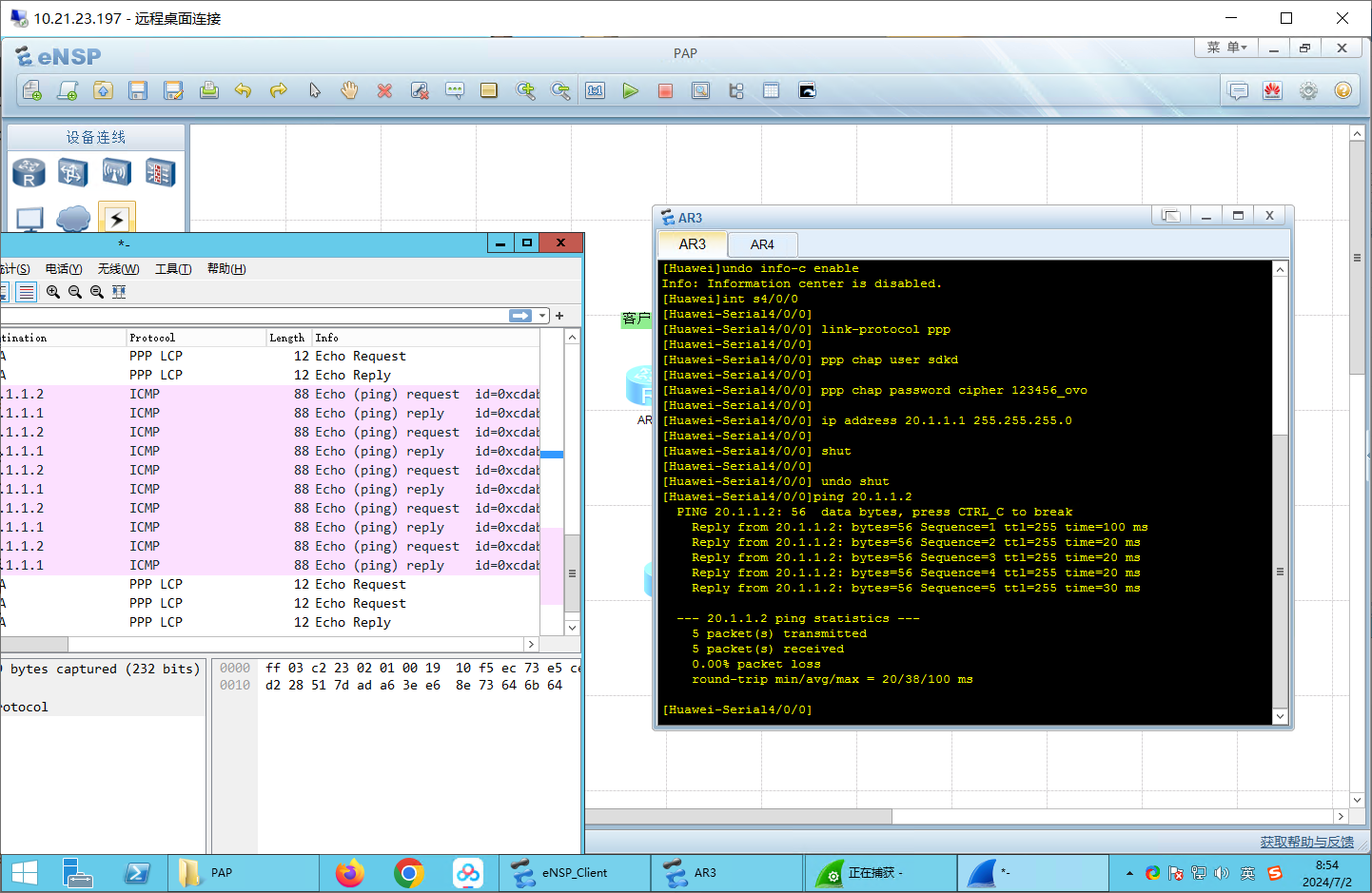
抓包握手
可以看到challenge和resp
challenge:
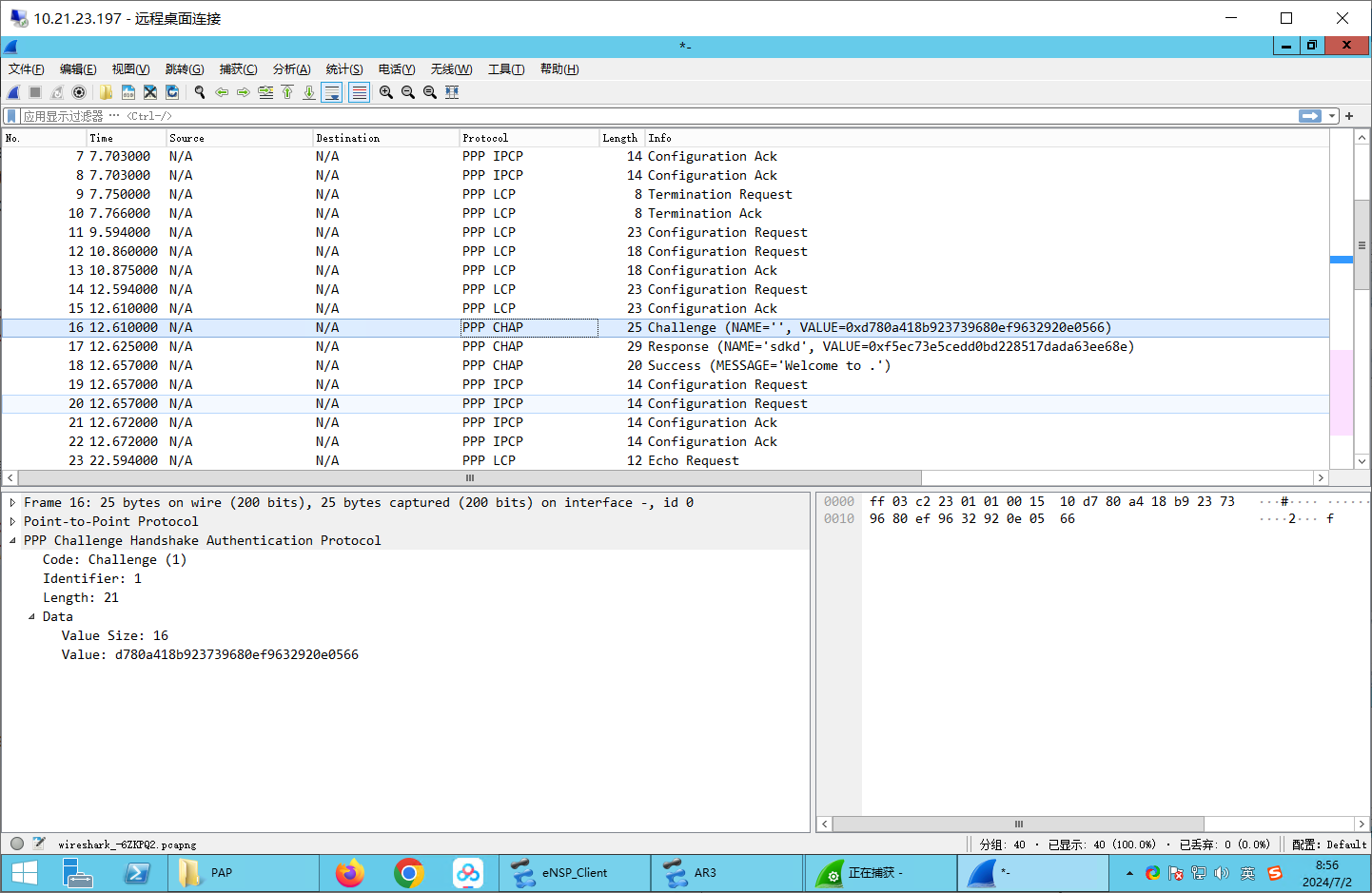
resp:
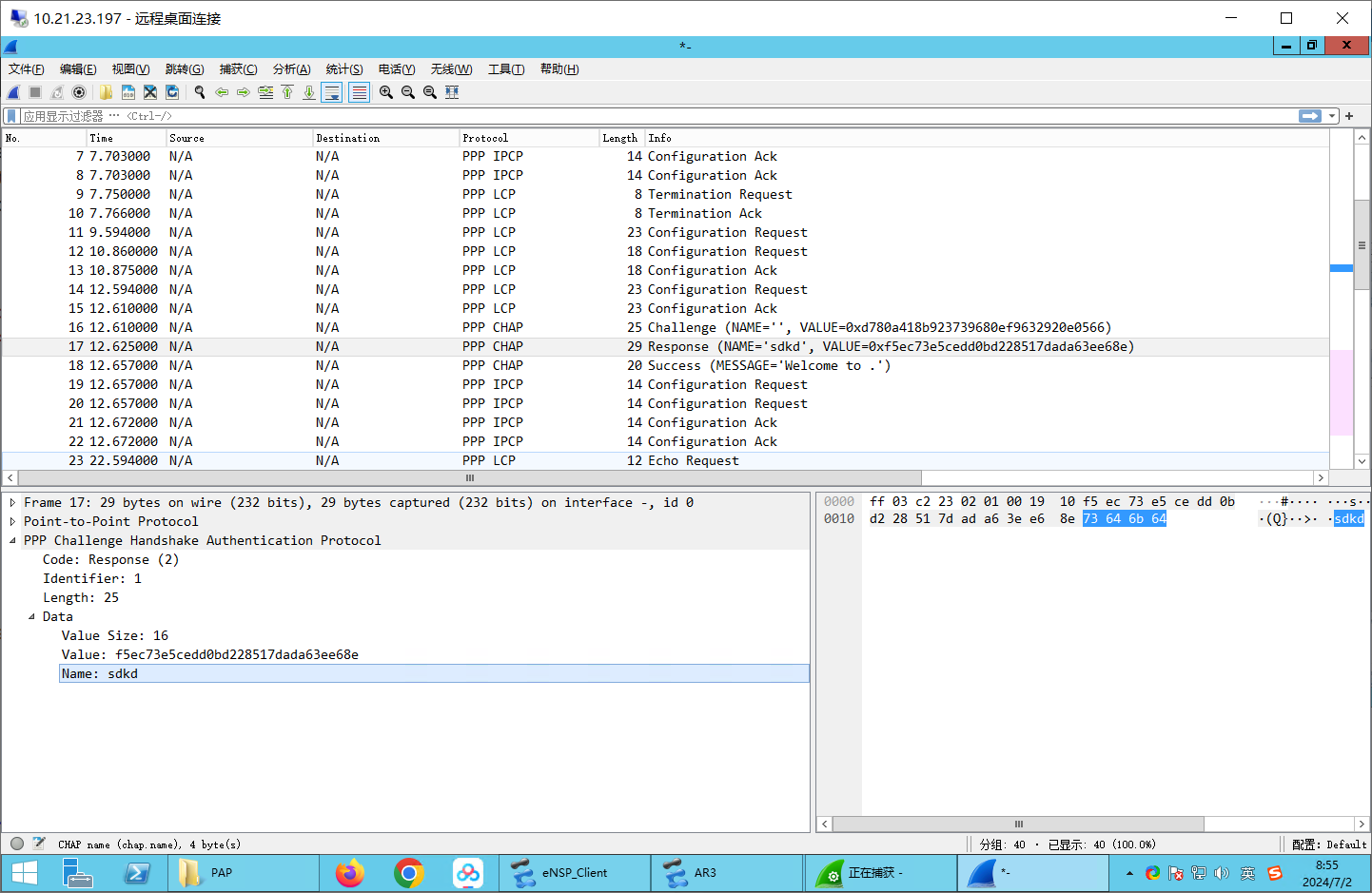
配置请求:
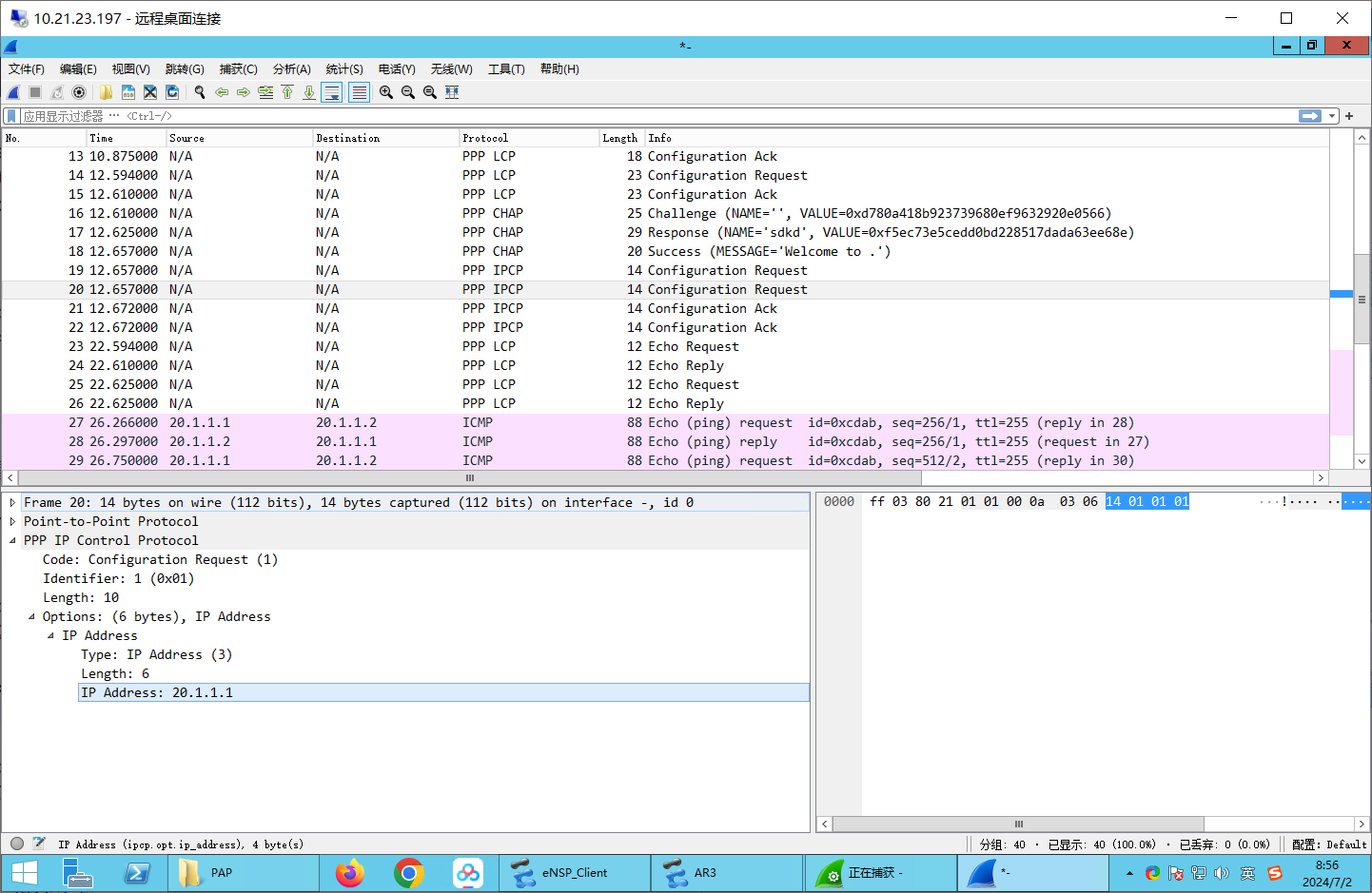
测试连接
ping 20.1.1.2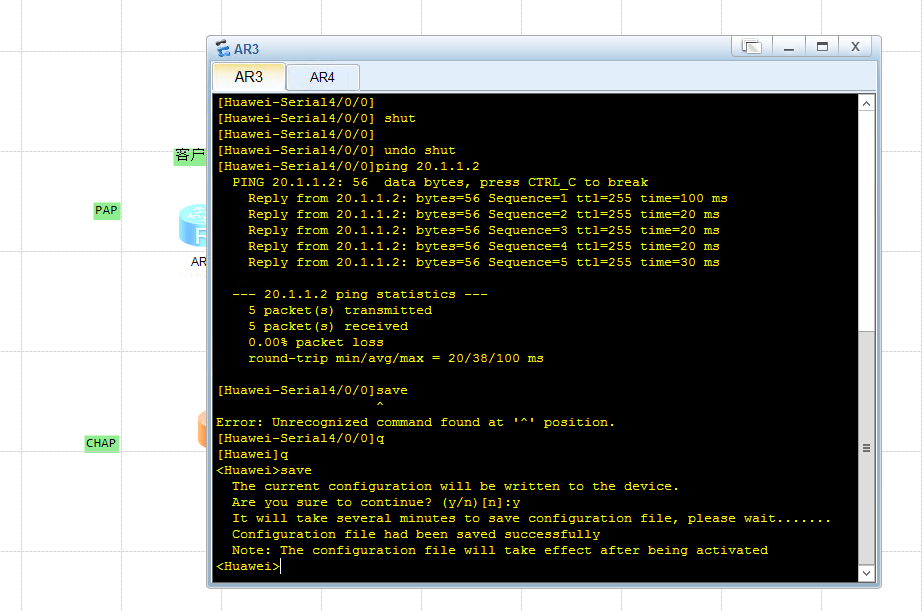
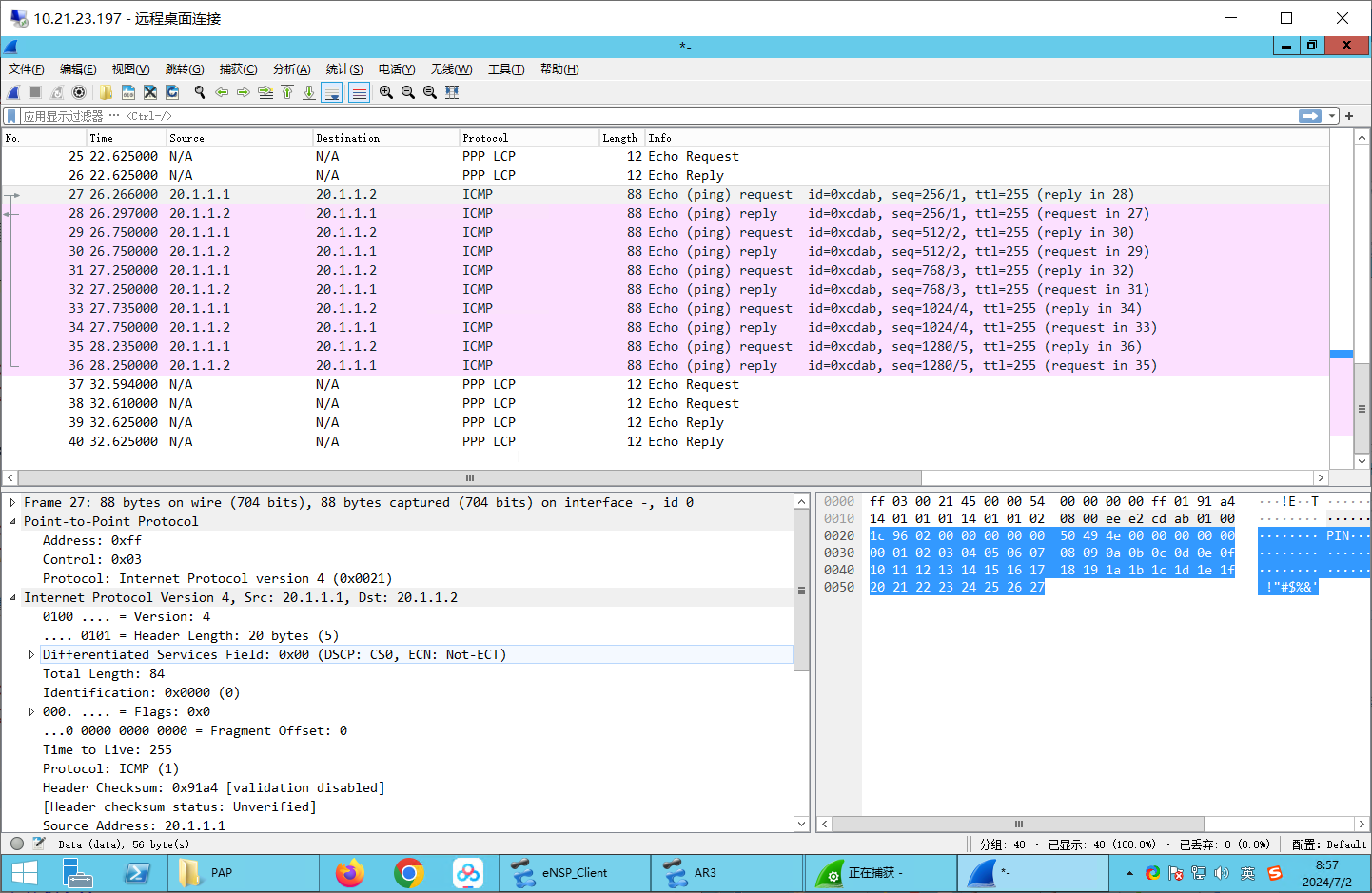
包含PPP层的ICMP包:
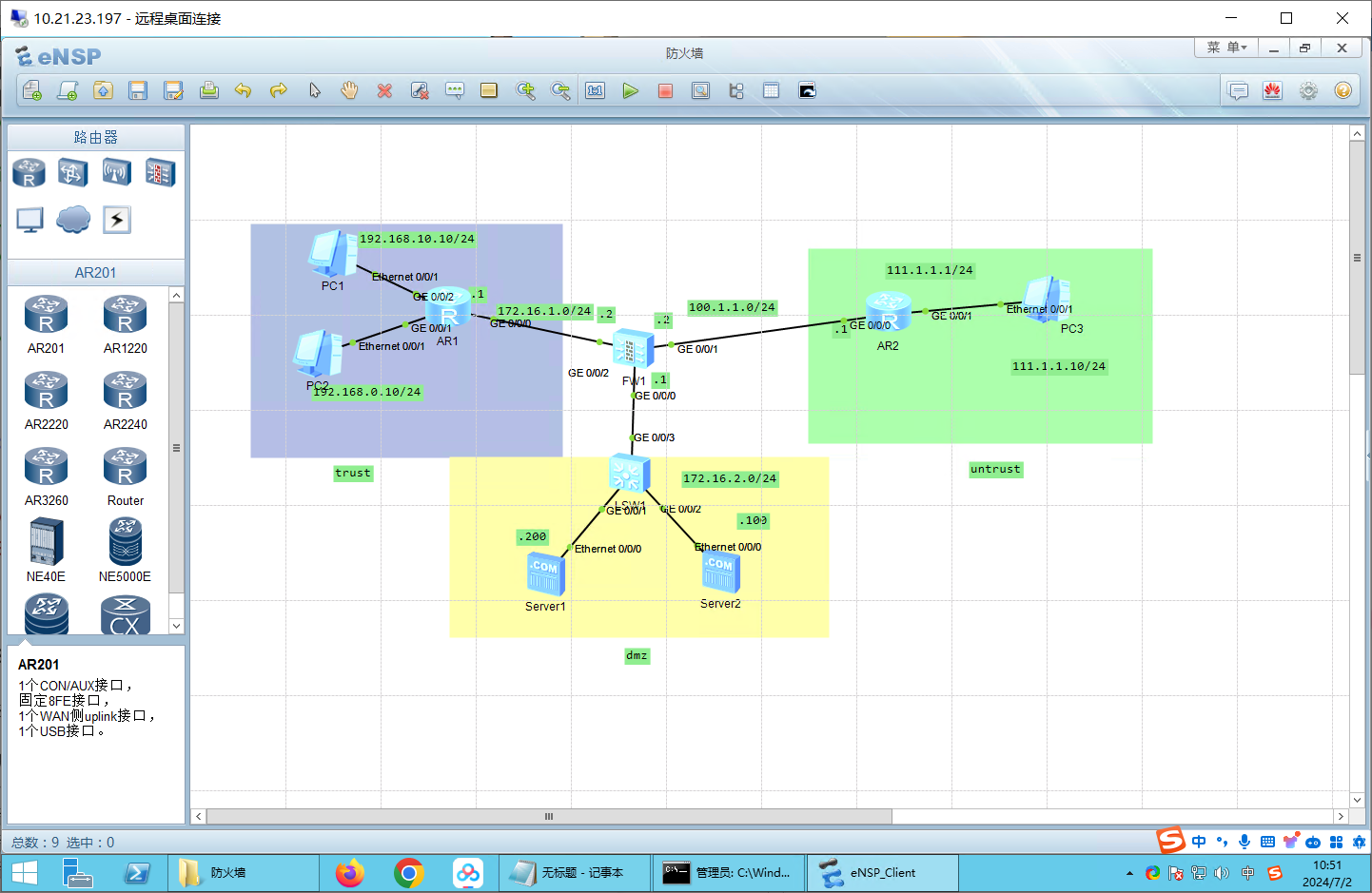
2、防火墙区域配置
致谢:胡芳同学
配置IP
网关都是.1
- 192.168.10.10/24
- 192.168.0.1/24
- 111.1.1.10/24
- 服务器:172.17.2.100/24
- 服务器:172.17.2.200/24
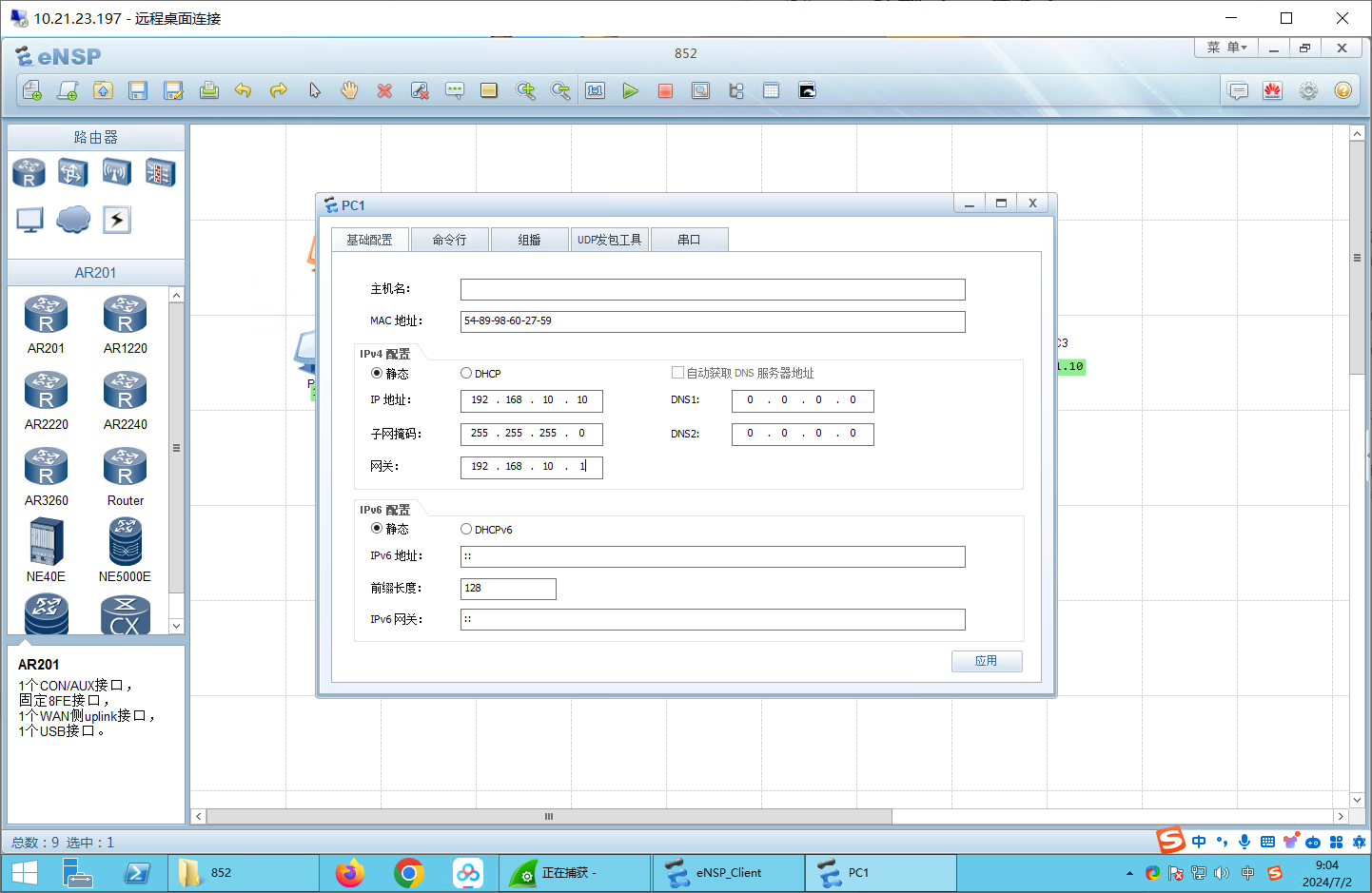
路由器配置IP
AR1
<Huawei>sys
Enter system view, return user view with Ctrl+Z.
[Huawei]undo info en
Info: Information center is disabled.
[Huawei]int g0/0/2
[Huawei-GigabitEthernet0/0/2]ip addr 192.168.10.1 24
[Huawei-GigabitEthernet0/0/2]int g0/0/1
[Huawei-GigabitEthernet0/0/1]ip addr 192.168.0.1 24
[Huawei-GigabitEthernet0/0/1]int g0/0/0
[Huawei-GigabitEthernet0/0/0]ip addr 172.16.1.1 24AR2:
<Huawei>sys
Enter system view, return user view with Ctrl+Z.
[Huawei]undo info en
Info: Information center is disabled.
[Huawei]int g0/0/0
[Huawei-GigabitEthernet0/0/0]ip addr 100.1.1.1 24
[Huawei-GigabitEthernet0/0/0]int g0/0/1
[Huawei-GigabitEthernet0/0/1]ip addr 111.1.1.1 24
[Huawei-GigabitEthernet0/0/1]ping 111.1.1.10
PING 111.1.1.10: 56 data bytes, press CTRL_C to break
Reply from 111.1.1.10: bytes=56 Sequence=1 ttl=128 time=110 ms
Reply from 111.1.1.10: bytes=56 Sequence=2 ttl=128 time=20 ms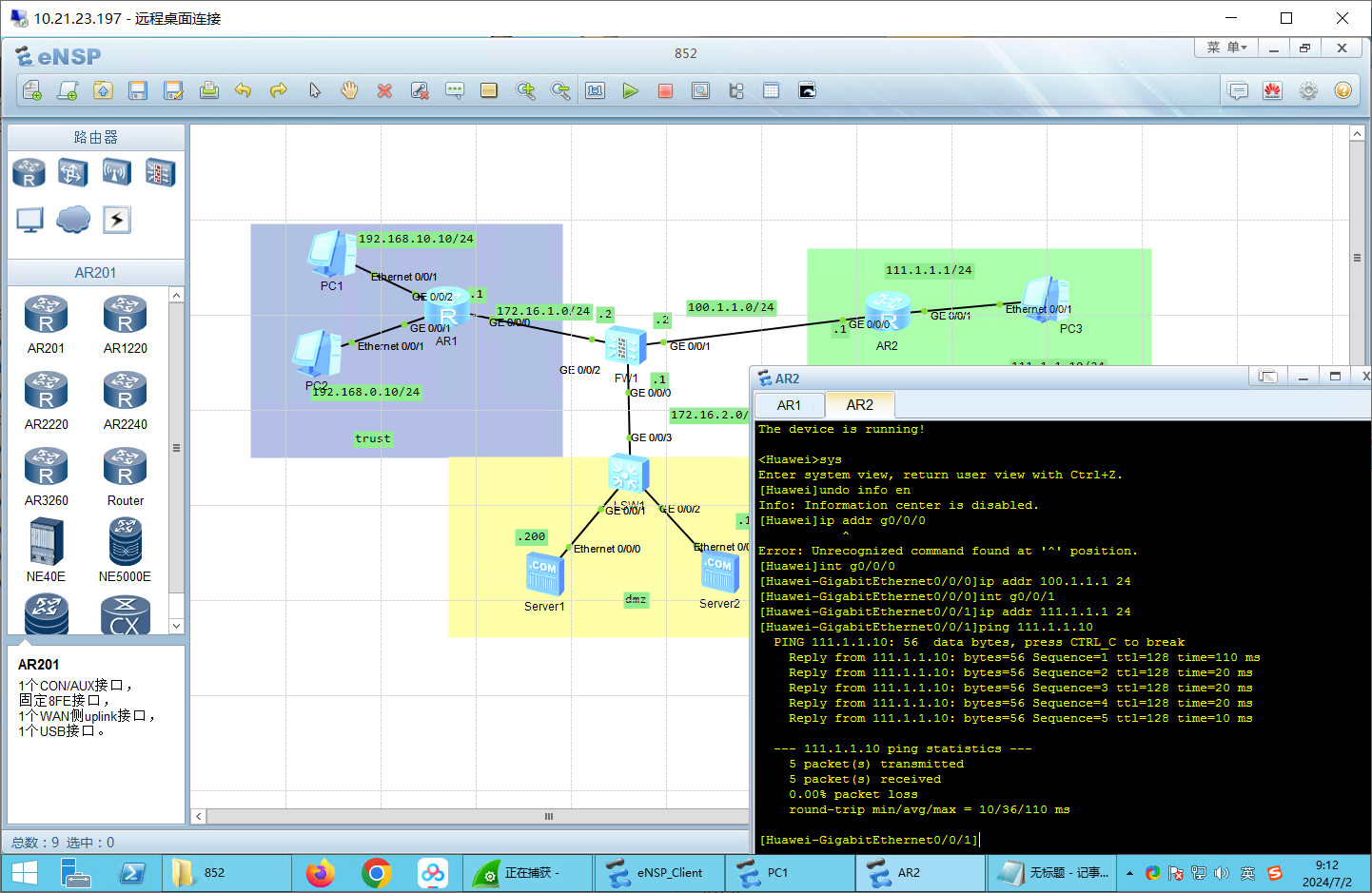
防火墙配置:
sys
undo info en
#DMZ
int G0/0/0
ip address 172.16.2.1 24
#untrust
int G0/0/1
ip address 100.1.1.2 24
# trust
int G0/0/2
ip address 172.16.1.2 24步骤二:路由配置
# AR1配置
ip route-static 0.0.0.0 0.0.0.0 172.16.1.2
# AR2配置
ip route-static 0.0.0.0 0.0.0.0 100.1.1.2
# 防火墙配置
ip route-static 192.168.0.0 255.255.255.0 172.16.1.1
ip route-static 192.168.10.0 255.255.255.0 172.16.1.1
ip route-static 111.1.1.0 255.255.255.0 100.1.1.1AR1: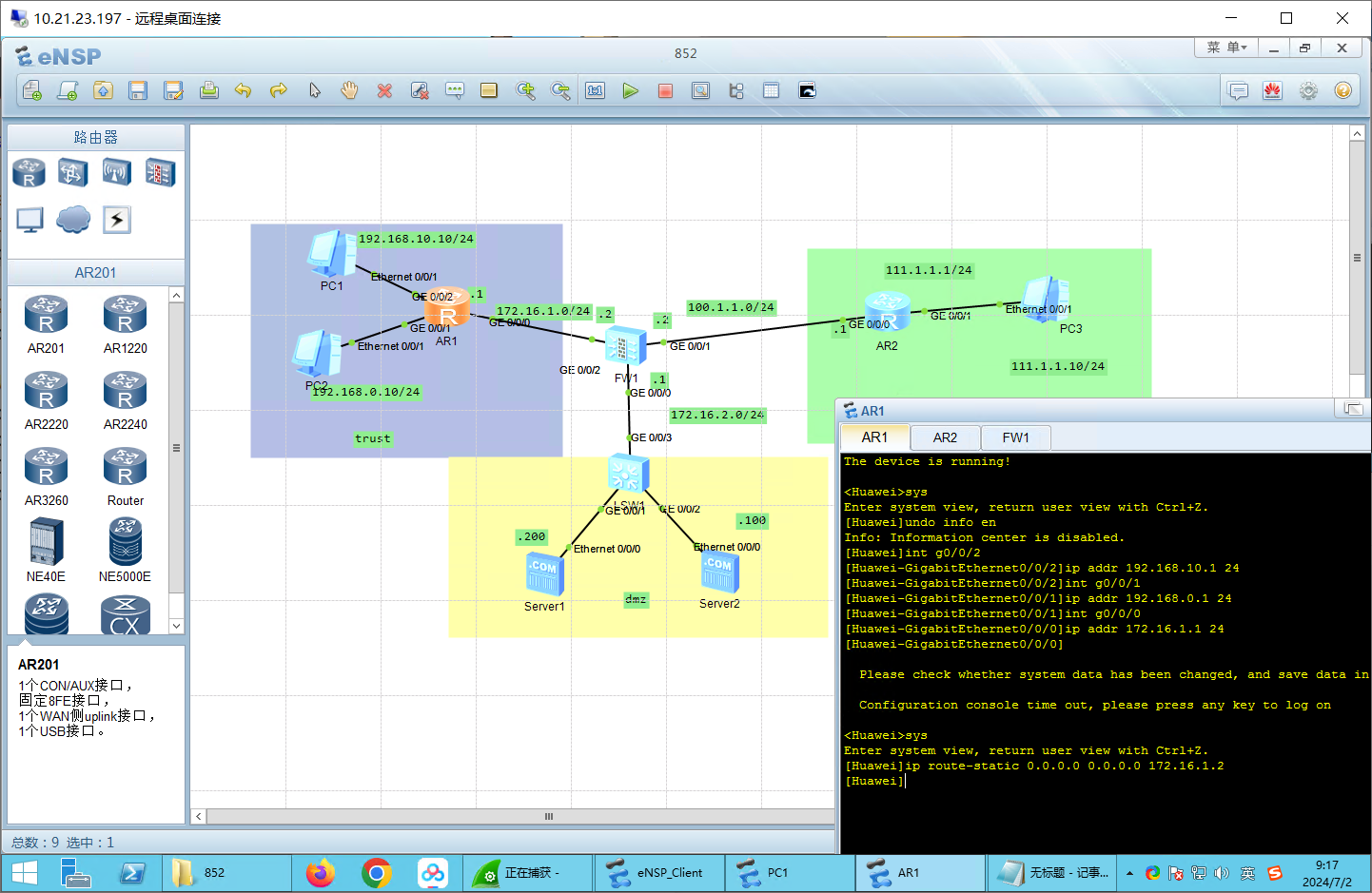
AR2: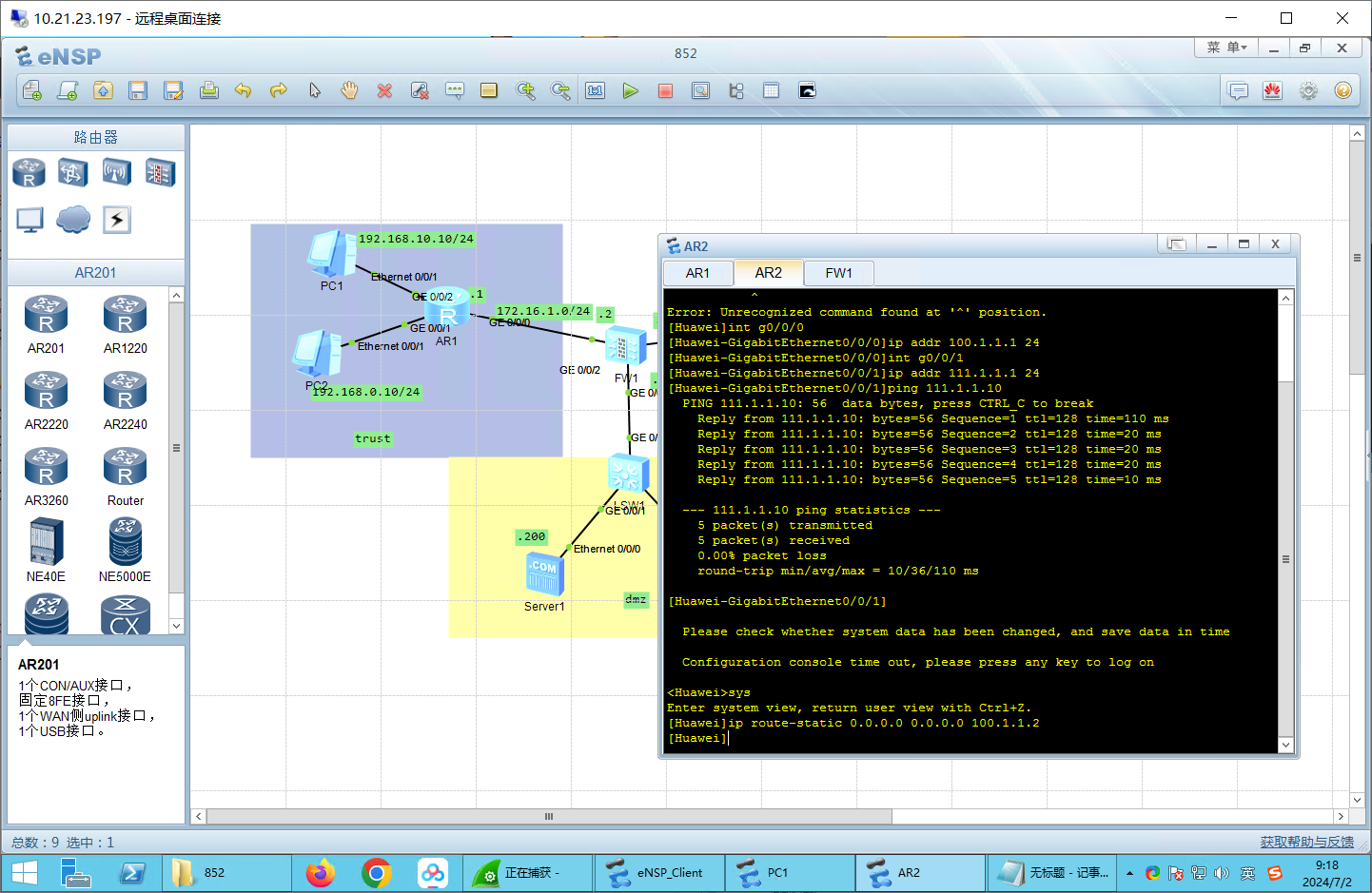
AR3: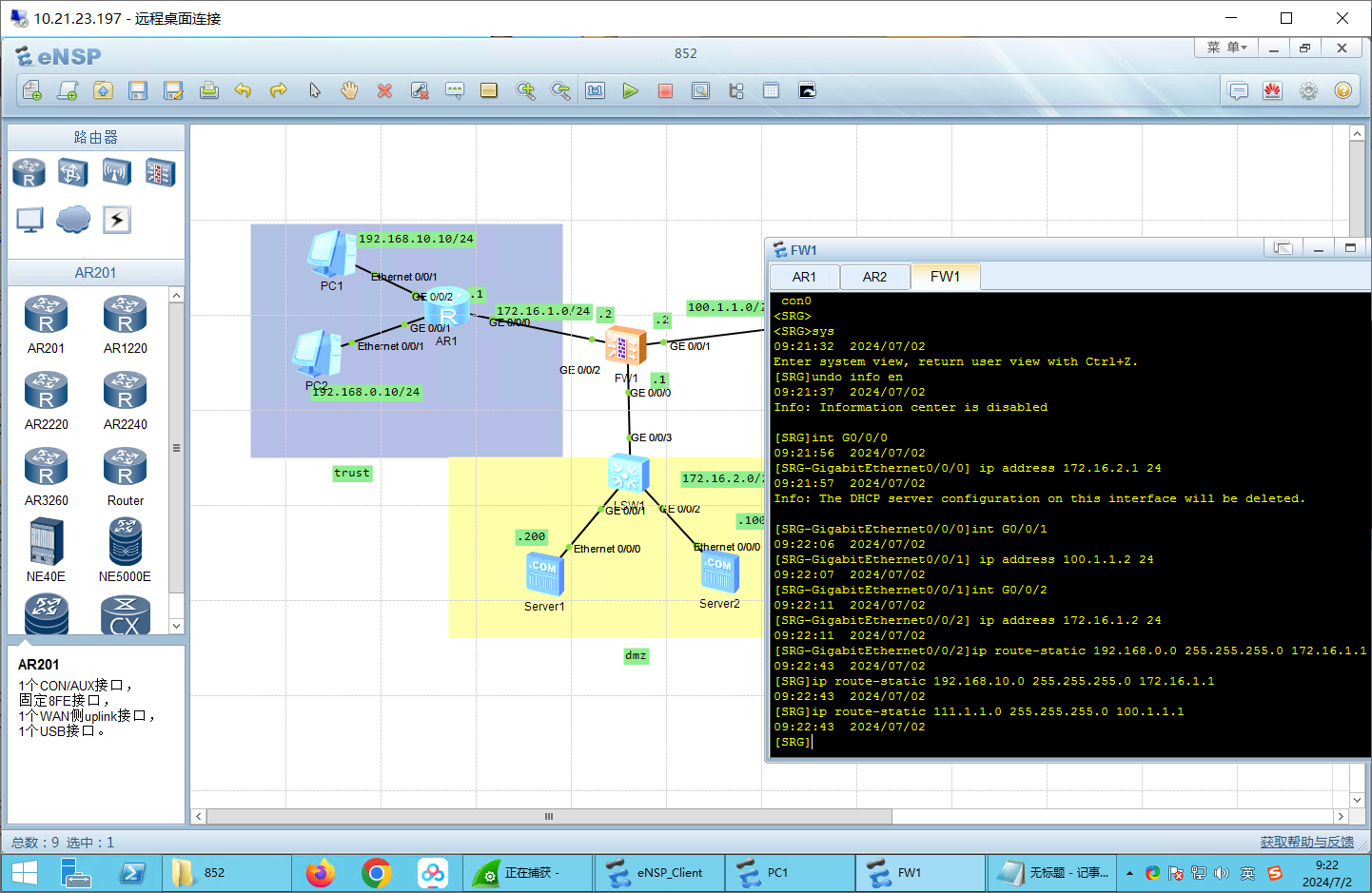
防火墙配置
# 1. 将接口加入相应的安全区域
firewall zone trust
add interface GigabitEthernet0/0/2
firewall zone untrust
add interface GigabitEthernet0/0/1
firewall zone dmz
add interface GigabitEthernet0/0/0
# 2. 配置安全区域间策略
policy interzone trust untrust outbound
policy 1
action permit
policy source 192.168.0.0 0.0.0.255
policy 2
action permit
policy source 192.168.10.0 0.0.0.255
policy interzone trust dmz outbound
policy 3
action permit
policy interzone dmz untrust outbound
policy 4
action permit
policy source 172.16.2.0 0.0.0.255
policy interzone dmz untrust inbound
policy 5
action permit
policy source 111.1.1.0 0.0.0.255
# 3. 小修:(可能不需要)
[SRG-policy-interzone-dmz-untrust-outbound-4]firewall zone dmz
10:34:30 2024/07/02
[SRG-zone-dmz]add interface GigabitEthernet0/0/0
10:34:36 2024/07/02
Info: The interface has been added to trust security zone.
[SRG-zone-dmz]firewall zone trust
10:34:46 2024/07/02
[SRG-zone-trust]undo add int g0/0/0
10:34:51 2024/07/02
[SRG-zone-trust]firewall zone dmz
10:35:02 2024/07/02
[SRG-zone-dmz]add interface GigabitEthernet0/0/0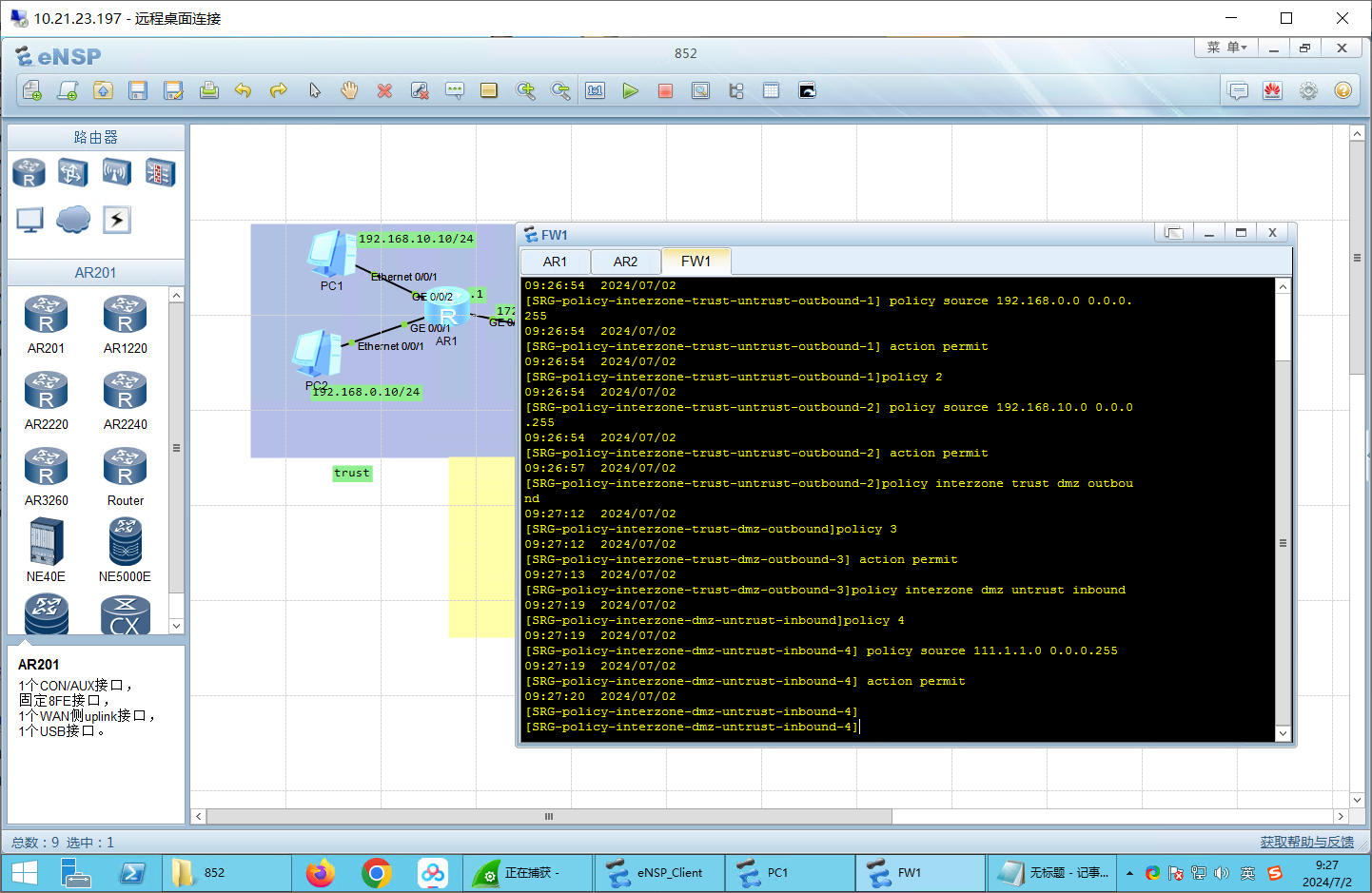
验证:验证配置
[SRG-zone-dmz]dis policy all
10:35:57 2024/07/02
policy zone local
#
policy zone trust
#
policy zone untrust
#
policy zone dmz
#
policy interzone local trust inbound
firewall default packet-filter is permit
#
policy interzone local trust outbound
firewall default packet-filter is permit
#
policy interzone local untrust inbound
firewall default packet-filter is deny
#
policy interzone local untrust outbound
firewall default packet-filter is permit
#
policy interzone local dmz inbound
firewall default packet-filter is deny
#
policy interzone local dmz outbound
firewall default packet-filter is permit
#
policy interzone trust untrust inbound
firewall default packet-filter is deny
#
policy interzone trust untrust outbound
firewall default packet-filter is deny
policy 1 (0 times matched)
action permit
policy service service-set ip
policy source 192.168.0.0 0.0.0.255
policy destination any
policy 2 (0 times matched)
action permit
policy service service-set ip
policy source 192.168.10.0 0.0.0.255
policy destination any
#
policy interzone trust dmz inbound
firewall default packet-filter is deny
#
policy interzone trust dmz outbound
firewall default packet-filter is deny
policy 3 (0 times matched)
action permit
policy service service-set ip
policy source any
policy destination any
#
policy interzone dmz untrust inbound
firewall default packet-filter is deny
policy 5 (0 times matched)
action permit
policy service service-set ip
policy source 111.1.1.0 0.0.0.255
policy destination any
#
policy interzone dmz untrust outbound
firewall default packet-filter is deny
policy 4 (0 times matched)
action permit
policy service service-set ip
policy source 172.16.2.0 0.0.0.255
policy destination any
#
[SRG-zone-dmz] 测试:trust->untrust可以ping通
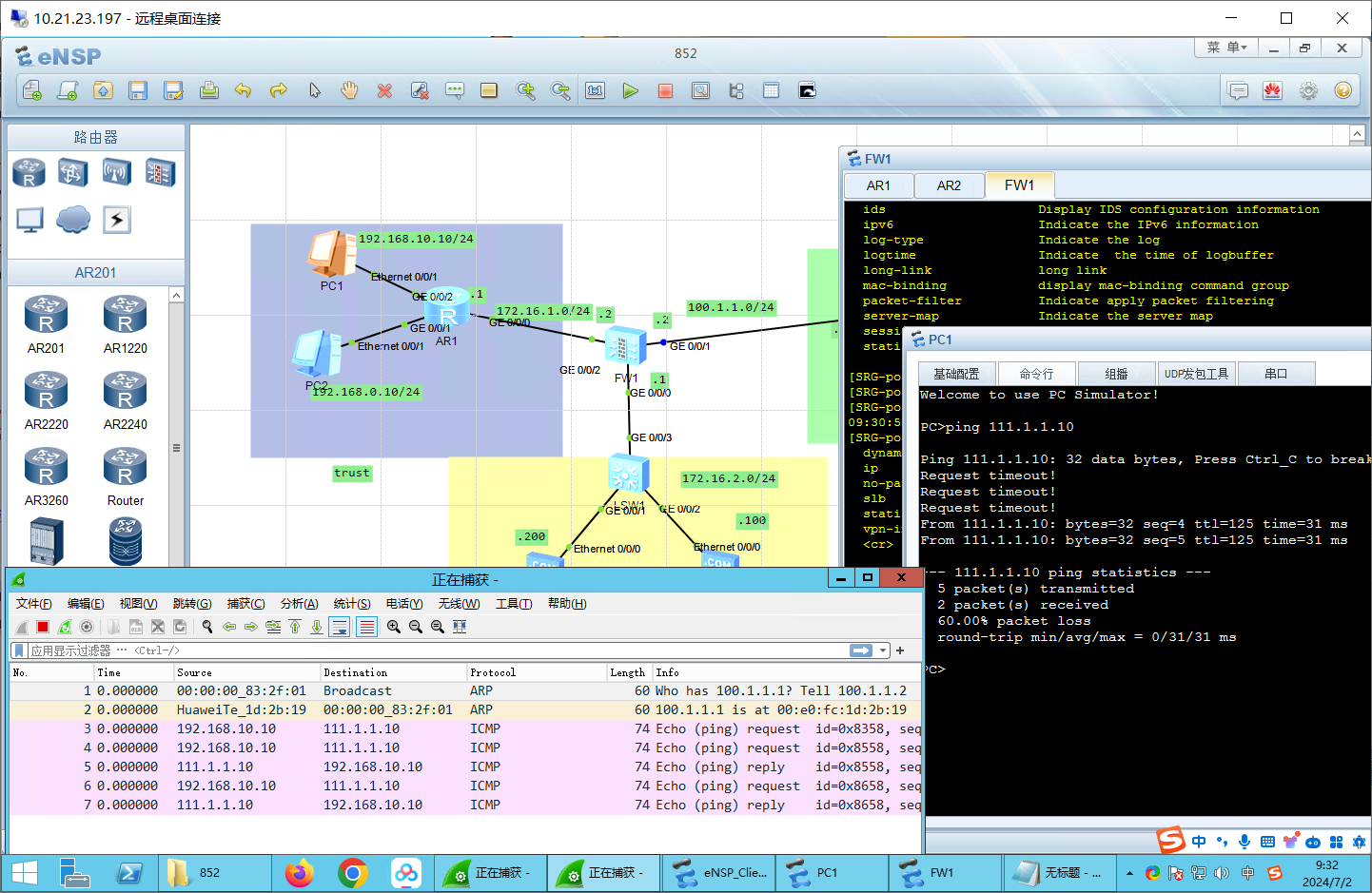
测试:trust->DMZ
ping 172.16.1.10可以ping通
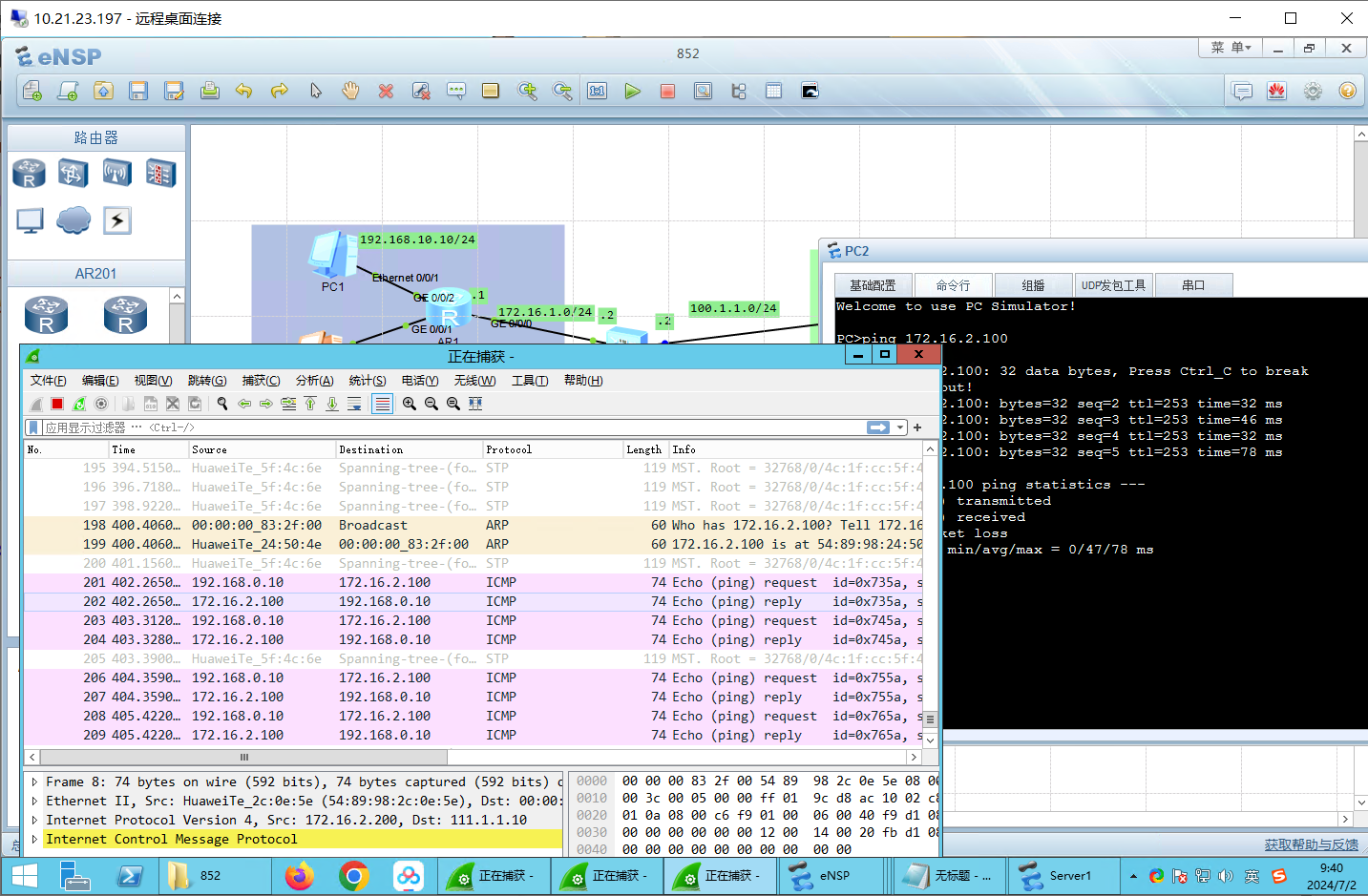
测试:untrust->DMZ
ping 172.16.2.100可以ping通。
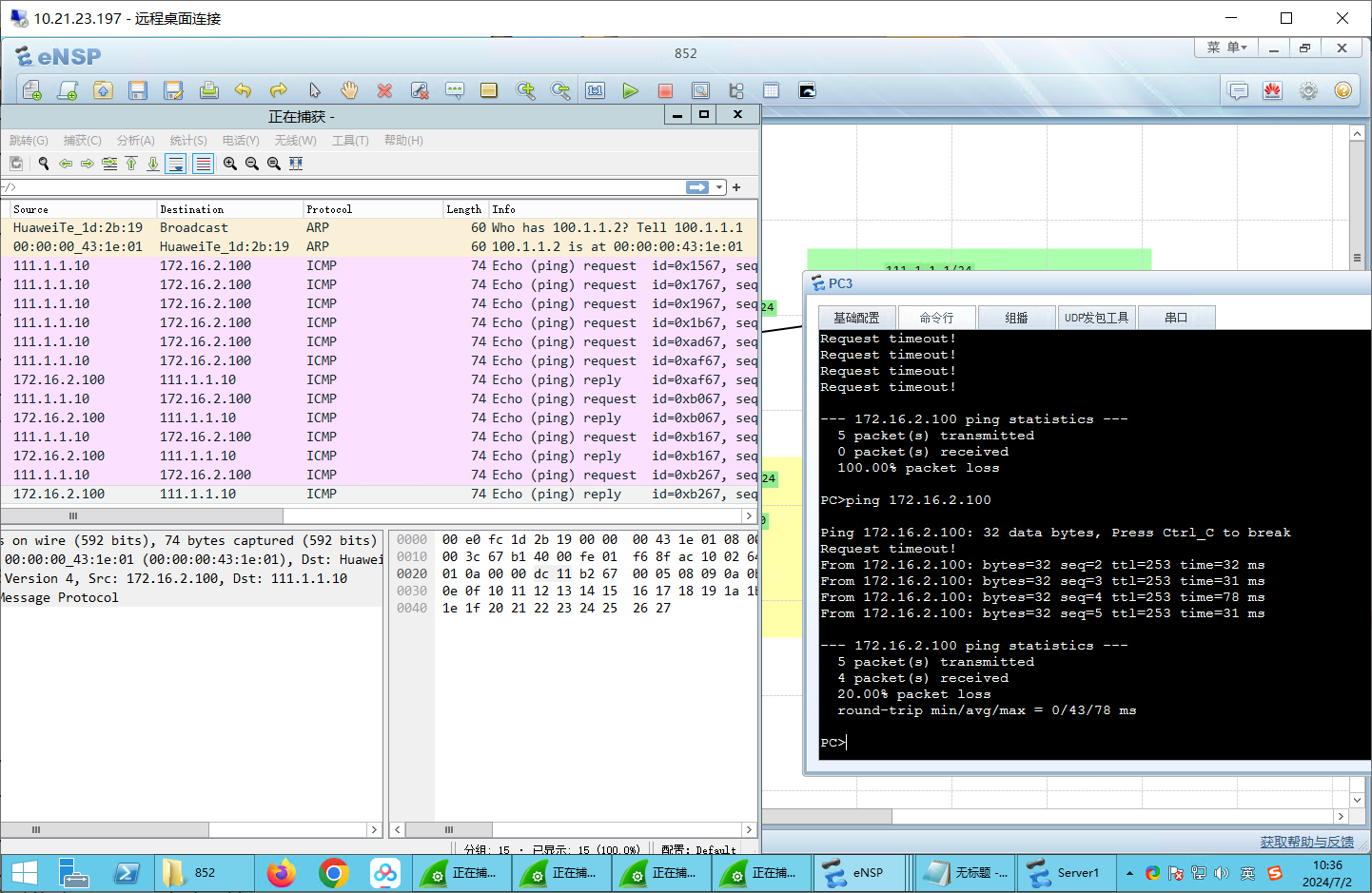
测试:DMZ->untrust
可以ping通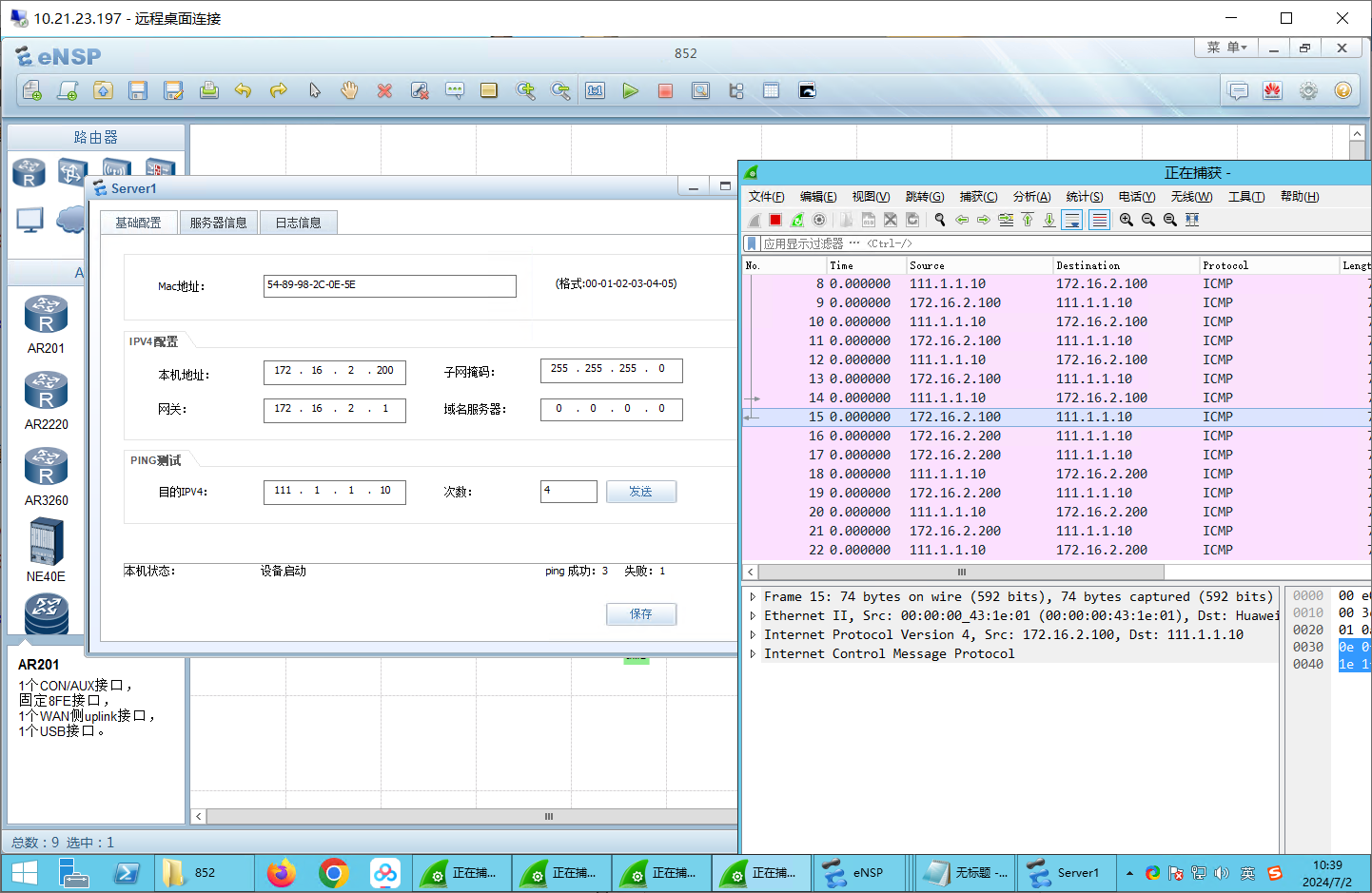
测试:untrust->trust
不可以ping通。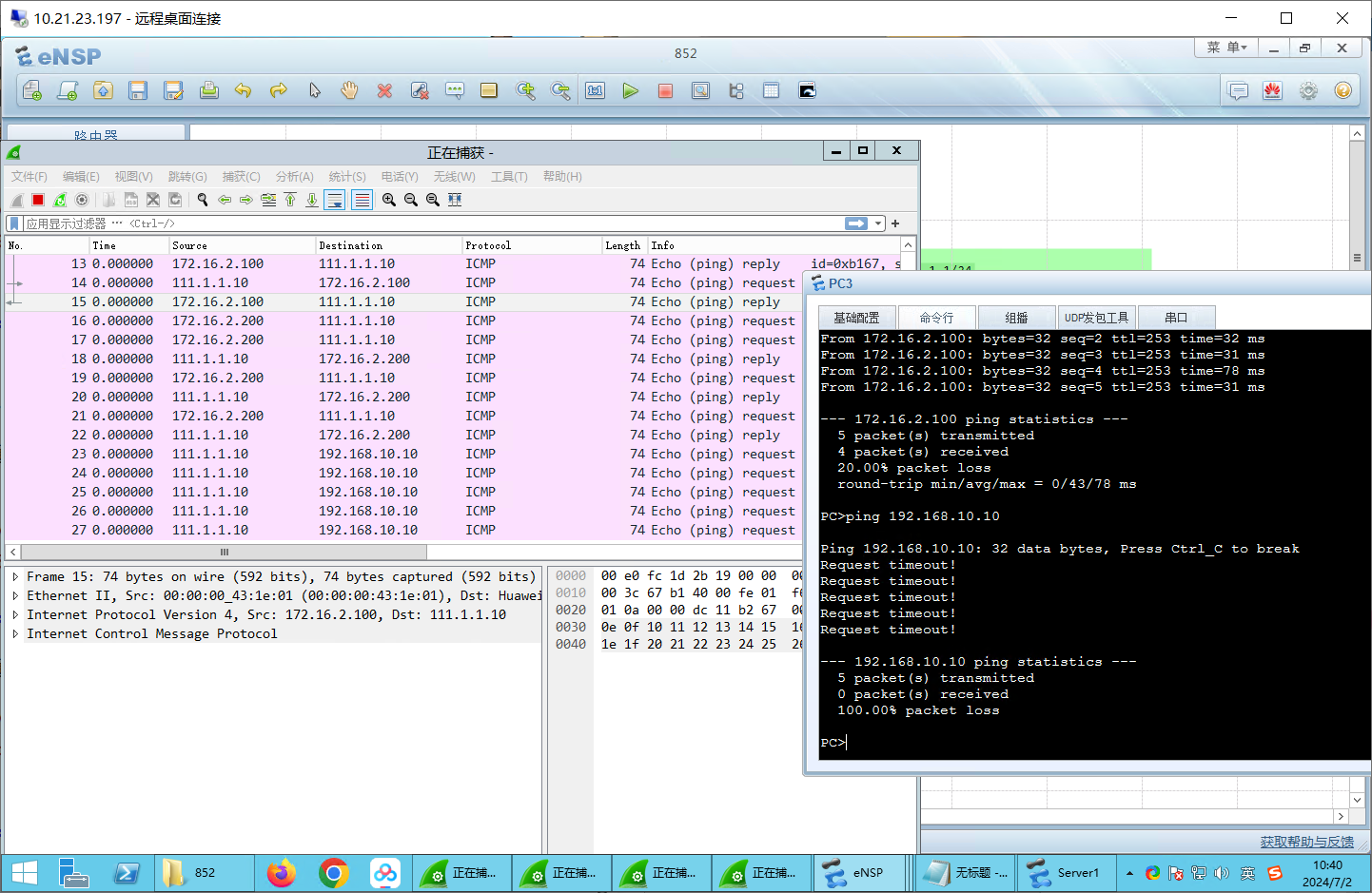
3、参考给定资料,设计山东科技大学校园网络(黄岛校区+泰安校区)。
以下内容已经包含在实验7中:
- 包含IPSEC隧道的设计(从公网转发私网流量)
- VLAN划分
- IP分配
配置文件
PAP
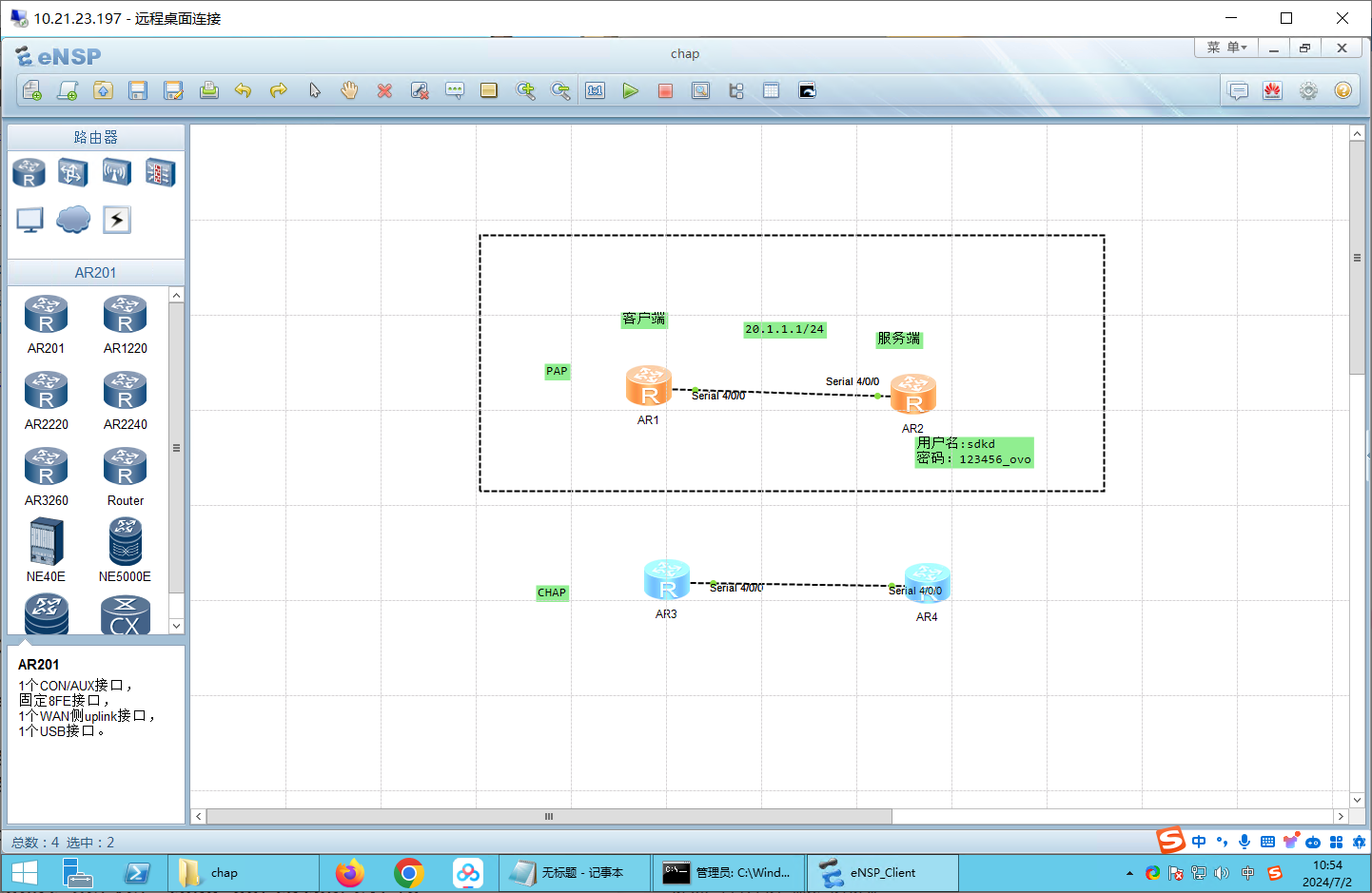
R1
[V200R003C00]
#
board add 0/4 2SA
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface Serial4/0/0
link-protocol ppp
ppp pap local-user sdkd password simple kd123456_ovo
ip address 20.1.1.1 255.255.255.0
#
interface Serial4/0/1
link-protocol ppp
#
interface GigabitEthernet0/0/0
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
returnR2
[V200R003C00]
#
board add 0/4 2SA
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user sdkd password cipher %$%$aRgKFvmdY5t[EEG6xQgR6Y]{%$%$
local-user sdkd service-type ppp
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface Serial4/0/0
link-protocol ppp
ppp authentication-mode pap
ip address 20.1.1.2 255.255.255.0
#
interface Serial4/0/1
link-protocol ppp
#
interface GigabitEthernet0/0/0
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
returnCHAP
R3
[V200R003C00]
#
board add 0/4 2SA
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
undo info-center enable
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface Serial4/0/0
link-protocol ppp
ppp chap user sdkd
ppp chap password cipher %$%$r|/!ZFhr=BZ4PC;fs\|A,.[a%$%$
ip address 20.1.1.1 255.255.255.0
#
interface Serial4/0/1
link-protocol ppp
#
interface GigabitEthernet0/0/0
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
returnR4
[V200R003C00]
#
board add 0/4 2SA
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
undo info-center enable
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user sdkd password cipher %$%$K0ne%.\pC$}kUuO2,bo=6i"K%$%$
local-user sdkd service-type ppp
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface Serial4/0/0
link-protocol ppp
ppp authentication-mode chap
ip address 20.1.1.2 255.255.255.0
#
interface Serial4/0/1
link-protocol ppp
#
interface GigabitEthernet0/0/0
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return防火墙
AR1
[V200R003C00]
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
undo info-center enable
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 172.16.1.1 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 192.168.0.1 255.255.255.0
#
interface GigabitEthernet0/0/2
ip address 192.168.10.1 255.255.255.0
#
interface NULL0
#
ip route-static 0.0.0.0 0.0.0.0 172.16.1.2
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
returnAR2
[V200R003C00]
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
undo info-center enable
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 100.1.1.1 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 111.1.1.1 255.255.255.0
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
ip route-static 0.0.0.0 0.0.0.0 100.1.1.2
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
returnFW1
# CLI_VERSION=V300R001
# Last configuration was changed at 2024/07/02 10:43:58 from console0
#*****BEGIN****public****#
#
stp region-configuration
region-name e05b8d1560bc
active region-configuration
#
interface GigabitEthernet0/0/0
alias GE0/MGMT
ip address 172.16.2.1 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 100.1.1.2 255.255.255.0
#
interface GigabitEthernet0/0/2
ip address 172.16.1.2 255.255.255.0
#
interface GigabitEthernet0/0/3
#
interface GigabitEthernet0/0/4
#
interface GigabitEthernet0/0/5
#
interface GigabitEthernet0/0/6
#
interface GigabitEthernet0/0/7
#
interface GigabitEthernet0/0/8
#
interface NULL0
alias NULL0
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/2
#
firewall zone untrust
set priority 5
add interface GigabitEthernet0/0/1
#
firewall zone dmz
set priority 50
add interface GigabitEthernet0/0/0
#
aaa
local-user admin password cipher %$%$)]`69::R3YFdi.SeqA[<66-$%$%$
local-user admin service-type web terminal telnet
local-user admin level 15
authentication-scheme default
#
authorization-scheme default
#
accounting-scheme default
#
domain default
#
#
nqa-jitter tag-version 1
#
ip route-static 111.1.1.0 255.255.255.0 100.1.1.1
ip route-static 192.168.0.0 255.255.255.0 172.16.1.1
ip route-static 192.168.10.0 255.255.255.0 172.16.1.1
#
banner enable
#
user-interface con 0
authentication-mode none
user-interface vty 0 4
authentication-mode none
protocol inbound all
#
slb
#
right-manager server-group
#
sysname SRG
#
l2tp domain suffix-separator @
#
firewall packet-filter default permit interzone local trust direction inbound
firewall packet-filter default permit interzone local trust direction outbound
firewall packet-filter default permit interzone local untrust direction outbound
firewall packet-filter default permit interzone local dmz direction outbound
#
ip df-unreachables enable
#
firewall ipv6 session link-state check
firewall ipv6 statistic system enable
#
dns resolve
#
firewall statistic system enable
#
pki ocsp response cache refresh interval 0
pki ocsp response cache number 0
#
undo dns proxy
#
license-server domain lic.huawei.com
#
web-manager enable
#
policy interzone trust untrust outbound
policy 1
action permit
policy source 192.168.0.0 0.0.0.255
policy 2
action permit
policy source 192.168.10.0 0.0.0.255
#
policy interzone trust dmz outbound
policy 3
action permit
#
policy interzone dmz untrust inbound
policy 5
action permit
policy source 111.1.1.0 0.0.0.255
#
policy interzone dmz untrust outbound
policy 4
action permit
policy source 172.16.2.0 0.0.0.255
#
return
#-----END----#0xff:文件下载
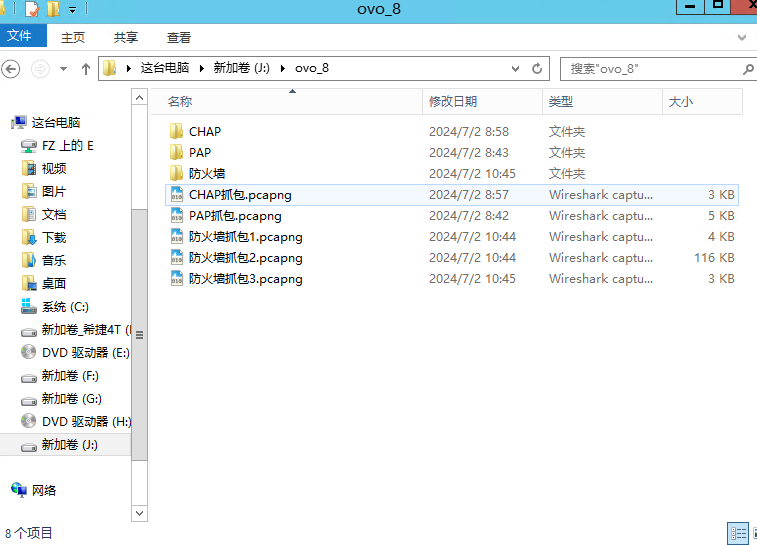
J:\ovo_8>tree /F
卷 新加卷 的文件夹 PATH 列表
卷序列号为 000000F0 5678:35C2
J:.
│ CHAP抓包.pcapng
│ PAP抓包.pcapng
│ 防火墙抓包1.pcapng
│ 防火墙抓包2.pcapng
│ 防火墙抓包3.pcapng
│
├─CHAP
│ │ r3.cfg
│ │ r4.cfg
│ │
│ └─chap
│ │ chap.topo
│ │
│ ├─904055DB-1C22-4e4c-AB05-6EBF512F02F
│ │ vrpcfg.zip
│ │
│ ├─90F0680A-37F0-4b02-B8DD-BB8267B411C
│ │ vrpcfg.zip
│ │
│ ├─97A89D3E-A69F-46ae-B21E-650ECB146AE
│ │ vrpcfg.zip
│ │
│ └─F7B890C7-DFF3-4e91-B891-5A93B8AAF64
│ vrpcfg.zip
│
├─PAP
│ │ R1.cfg
│ │ R2.cfg
│ │
│ └─PAP
│ │ PAP.topo
│ │
│ ├─97A89D3E-A69F-46ae-B21E-650ECB146AE
│ │ vrpcfg.zip
│ │
│ └─F7B890C7-DFF3-4e91-B891-5A93B8AAF64
│ vrpcfg.zip
│
└─防火墙
│ AR1.cfg
│ AR2.cfg
│ FW1.cfg
│
└─防火墙
│ 防火墙.topo
│
├─0220F2E4-47A2-486c-AD46-0D4769CE219
│ vrpcfg.zip
│
├─1AF76E92-D68A-4057-965D-3B6452594CE
│ PC.xml
│
├─6AE4406A-7116-4c99-972C-A2880B823B5
│ vrpcfg.zip
│
├─85DAA1A7-7D9C-4867-963B-C77C20308B0
│ flash.efz
│
├─86D4A863-1037-4f1b-9FFA-6F180DD7CFE
│ flash.efz
│
└─BABEBE9B-5DF1-4707-AE63-67BC804ACC0
PC.xml
J:\ovo_8>
建议多用口语化表达,拉近与读者距离。
这篇文章不错!